 Table of Contents
Table of Contents
Introduction
Consider a workplace where everyone takes cybersecurity seriously, from the CEO to the newest team member. In this environment, security isn’t just about ticking boxes—it’s an embedded part of the company’s DNA.
Today, even the most sophisticated defenses are vulnerable to simple human mistakes. But a strong security culture does more than just support these systems; it empowers everyone to become a proactive guardian against cyber threats. It also builds trust among stakeholders, demonstrating a deep commitment to protecting your company’s resources and the confidentiality and interests of those they serve. In this context, growing a strong information security culture is more than a strategic move, it’s the foundation for cyber resilience and business growth.
Growing a strong information security culture is more than a strategic move. It’s the foundation for cyber resilience and business growth.
This guide from SaltyCloud outlines the steps necessary to build and maintain an information security culture. From engaging leadership to onboarding new team members, it explores how to instill a mindset that values cybersecurity as a critical component of business health. It also provides practical strategies for enhancing cybersecurity awareness, aligning with the latest cybersecurity practices, and ensuring that every stakeholder understands their role in safeguarding the organization’s information landscape.
What is information security culture?
Understanding “information security culture” is crucial for businesses to strengthen their defenses against digital threats. Though extensively discussed in academic circles, this concept calls for a clear definition that aligns with academic and practical realms.
The work of Adéle da Veiga, Liudmila V. Astakhova, Adéle Botha, and Marlien Herselman in “Defining Organizational Information Security Culture — Perspectives from Academia and Industry,” published by Computers & Security in 2020, offers a definition that bridges these perspectives. The authors combined extensive literature reviews and survey responses from 512 industry professionals to arrive at this definition.
Academic definition
According to the authors’ in-depth study, information security culture refers to people’s organizational behavior as they interact with and protect information systems. It’s about implementing requirements and aligning subsequent actions with the organization’s information security policies. Continuous communication, awareness, training, and educational initiatives ultimately foster an information security culture.
Information security culture refers to people’s behavior in interacting with and protecting information systems within an organization.
Theoretically, these practices will become ingrained in the workforce as part of the organizational ethos. Employees’ beliefs, values, knowledge, and attitudes toward protecting information assets will shape them over time. Senior management’s vision, backed by a robust ICT environment, also plays a critical role in this kind of culture. The result is a trustworthy environment that upholds its integrity with stakeholders.
Here is the full definition for context:
“Information security culture is contextualized to the behavior of humans in an organizational context to protect information processed by the organization through compliance with the information security policy and procedures and an understanding of how to implement requirements in a cautious and attentive manner as embedded through regular communication, awareness, training, and education initiatives.
The behavior over time becomes part of the way things are done, i.e., second nature, as a result of employee assumptions, values, and beliefs, and their knowledge and attitude towards and perception of the protection of information assets. The information security culture is directed by the vision of senior management together with management support in line with the department and information security policy and influenced through internal and external factors, supported by an adequate ICT environment, visible in the artifacts of the organization and behavior exhibited by employees, thereby creating an environment of trust with stakeholders and establishing integrity.” (da Veiga, Astakhova, Botha, & Herselman, 2020).
An information security culture is fostered through continuous communication, awareness, training, and educational initiatives.
Layman definition
In simpler terms, information security culture is an organization’s collective effort to protect its information assets. It’s a mindset that permeates every employee’s daily behaviors, attitudes, and practices, ensuring a vigilant approach to security and risk management. This type of culture is more than policy adherence; it’s about integrating security awareness into every aspect of the organization’s operations.
Information security culture is a mindset that permeates every employee’s daily behaviors, attitudes, and practices, ensuring a vigilant approach to security and risk management.
Continuously nurtured by communication, training, and education and guided by senior management’s strategic vision, a strong information security culture is a proactive, systematic approach. It combines technology support to enable the organization to handle and recover from information security threats effectively. This not only fosters internal trust but also builds integrity outside the organization.
In summary, information security culture is about instilling a security-first mindset throughout the organization from the top down. It ensures that every team member naturally prioritizes the protection of information assets, reinforcing the organization’s overall defense against digital threats and attacks.
Foundational principles of a strong security culture
An effective security culture typically comprises the following key components:
- Policies and procedures: The foundation of a solid information security culture lies in clear, user-friendly policies and procedures that outline safe conduct for day-to-day operations.
- Leadership commitment: A culture of information security flourishes when it starts from the top. Leadership must prioritize and visibly support information security initiatives and lead by example.
- Employee education: For information security culture to truly take root, your organization must provide continuous, engaging training and education that resonates with employees across various departments.
- Communication and collaboration: Open lines of communication are essential in a strong culture of information security. Collaboration across departments ensures a unified approach to cybersecurity, breaking down silos that can lead to vulnerabilities.
- Regular monitoring and improvement: An effective information security culture is not static; it requires ongoing evaluation and refinement. Continuous improvement also signals to employees that security is worth investing time and resources into.
- Technology solutions: Leveraging the right solutions is crucial for supporting your organization’s information security culture. However, technology alone is not a silver bullet—it must be integrated into the broader context of the organization’s information security culture, with proper training and policies to guide its use.
Operationalizing information security culture
Operationalizing information security culture means taking the foundational principles of information security culture off the paper and weaving them into the very fabric of your everyday business operations to enable a sustainable security culture.
Implementing governance and policies
Transforming policies and procedures from documents into daily practice is key to operationalizing an information security culture. Here’s how your organization can effectively implement these guidelines:
- Make policies accessible and understandable: Ensure all security policies and procedures are accessible to every employee, ideally through a centralized digital platform. Use clear, concise language to explain each policy’s rationale and importance to your organization’s security. This clarity helps employees understand what to do and why it matters.
- Integrate policies into onboarding and regular training: Embed information security policies into the onboarding process for new hires and incorporate them into ongoing training programs. Regularly revisiting these policies helps reinforce their significance and ensures that security practices stay fresh in employees’ minds. Tailoring training scenarios to reflect real-life situations can also help employees better understand how to apply policies in their daily work.
- Monitor compliance and provide feedback: Establish mechanisms to monitor compliance with security policies and procedures. This could involve regular audits, security risk assessments, or even simple check-ins. Feedback loops are essential; when employees know how they’re doing and where they can improve, it fosters a culture of continuous improvement. Recognizing and rewarding compliance can motivate employees to adhere to established guidelines, further embedding security practices into the organizational culture.
Getting leadership on board
For an information security culture to thrive, securing the commitment of your leaders is not just the first step; it’s a continuous process. Here’s how companies are to ensure leadership gets on board and stays actively involved:
- Present clear data and case studies: Present leaders with compelling data on the risks and potential impacts of security issues threats alongside case studies of successful security cultures and cautionary tales of neglect. Real-world examples can highlight the tangible benefits of proactive security measures and the dire consequences of inaction.
- Integrate security goals with business objectives: Demonstrate how information security aligns with your organization’s broader business goals. By linking security initiatives directly to business outcomes, such as customer trust and operational continuity, you can make a persuasive argument for prioritizing cybersecurity investments.
- Involve leaders in security initiatives: Beyond just approval, involve leaders in cybersecurity initiatives through active roles in training, policy development, and public endorsements of security efforts. Their visible commitment can inspire a company-wide culture of security. Consider establishing a cross-departmental security steering committee that includes top executives. This committee can oversee the implementation of security policies, review security strategies, and ensure alignment with organizational objectives. It can serve as a symbol and a mechanism of leadership’s ongoing commitment to information security.
Putting employee engagement and security awareness at the forefront
Placing employee engagement at the heart of information security culture is essential for defending against cyber threats. Employees who are fully engaged and understand their role in protecting your organization become invaluable allies in the fight against data breaches. Active involvement leads to heightened vigilance and a proactive stance towards identifying and addressing security risks. Here’s how to ensure that every employee is informed and fully invested in your organization’s cybersecurity efforts:
- Foster a network of security advocates: Cultivate a security community comprised of dedicated security advocates across different departments. Start by identifying employees with a keen interest in cybersecurity and a knack for influencing their peers. By providing these advocates with specialized training, they can further their knowledge and become pivotal in spreading awareness and promoting secure behavior. Empower these individuals to act as liaisons between the security team and their departments, making security a topic of regular discussion and shared responsibility.
- Integrate security into daily operations: Make cybersecurity an integral part of everyday work life. This could mean incorporating security checklists into daily routines, using secure behaviors as criteria in performance reviews, or embedding security milestones into project timelines. Making security a constant, visible element of daily tasks ensures it becomes second nature to the workforce.
- Celebrate security successes: Acknowledge and reward secure behaviors and contributions to the organization’s cybersecurity. Whether through formal recognition programs, shout-outs in company meetings, or tangible rewards for reporting vulnerabilities, showing appreciation for security-conscious actions fosters a positive security culture. Recognizing these efforts motivates individuals and sets a standard for others to follow, reinforcing the importance of everyone’s role in maintaining security.
Promoting open and collaborative communication
Cultivating open and collaborative communication within your organization is crucial for growing and maintaining an information security culture. Such an environment encourages every team member to participate actively in the security dialogue, ensuring that concerns are raised, insights are shared, and collective learning is prioritized. Open communication demystifies cybersecurity and embeds it into the organizational fabric, making security a shared responsibility. Here’s how your organization can foster an atmosphere where communication enhances information security:
- Establish safe channels for reporting: Create confidential and accessible channels for employees to report security concerns without fear of reprisal. Emphasize that reporting is a constructive and encouraged action vital to the organization’s security. Regularly communicate the existence and purpose of these channels to all employees to ensure they know how and where to voice their concerns.
- Promote ownership and accountability: Encourage employees to embrace their role in the organization’s security efforts. Use training sessions, team meetings, and internal communications to highlight how individual actions contribute to the organization’s security posture. Growing a culture of accountability involves ensuring everyone understands the impact of their behavior on your organization’s security and encouraging proactive engagement with security protocols.
- Leverage collaborative platforms for knowledge sharing: Utilize collaboration platforms to share updates on potential threats, policy changes, and insights from security incidents. These platforms should be a space for open dialogue, where employees can ask questions, share observations, and learn from each other’s experiences. Regularly scheduling cross-departmental meetings or workshops focused on security can also foster a sense of community and shared purpose in defending against cyber threats.
Leveraging technology and tools
Technology and tools enhance your organization’s ability to detect and respond to threats and serve as educational platforms, transforming security incidents into valuable learning experiences. The right technology can streamline security processes, making it easier for employees to adopt secure practices and remain vigilant. Here’s how your organization can effectively leverage tools in its information security efforts:
- Governance, risk, and compliance (GRC) platforms: These platforms are the cornerstone of a sound security culture, providing a centralized location for managing all aspects of information security governance, risk, and compliance. By centralizing policies, controls, and assessment procedures, GRC platforms help embed regulatory awareness into the organizational ethos, ensuring everyone understands their role within the larger governance structure.
- Security awareness training platforms: Security awareness platforms deliver engaging and interactive training content, making learning about security accessible and exciting for all employees. Regular training sessions help keep security in mind, encouraging a vigilant and informed workforce that can recognize and respond to threats swiftly.
- Anonymous incident reporting platforms: An open culture is a secure culture. By providing a means for employees to report security concerns and incidents anonymously, these platforms encourage a more forthcoming and proactive approach to security. They serve as a safe outlet for staff to express security-related concerns, facilitating early detection of issues before they escalate while streamlining the process for information security teams.
Information security culture and information security risk management (ISRM)
Information Security Risk Management (ISRM) involves actively managing risks associated with information technology. It’s a collaborative effort involving multiple stakeholders working together to protect the confidentiality, integrity, and availability of their assets.
An information security culture is about cultivating a mindset where every team member views protecting information assets as their responsibility.
A sustainable security culture is the backbone of successful ISRM. It’s about cultivating a mindset where every team member views protecting information assets as their responsibility. This type of culture is necessary because it transforms cybersecurity from an abstract concept managed by a dedicated security team into a fundamental aspect of every employee’s daily activities. In essence, an information security culture ensures that proactive measures against cyber threats become second nature for every member of an organization.
The role of governance, risk, and compliance (GRC) platforms
Governance, risk, and compliance (GRC) platforms are essential tools for information security teams. They centralize governance, risk management, and compliance activities, making these processes more efficient and interconnected. GRC technologies democratize the security and compliance management process, making it a collective responsibility. When they can offer clear, intuitive interfaces and actionable insights, GRC platforms engage employees at all levels. This engagement facilitates a culture where everyone understands, values, and practices information security. The result is a proactive and security-conscious business environment.
Choosing the right GRC platform
Isora is a collaborative GRC platform that empowers everyone to own risk together, with user-friendly and flexible tools. With Isora, teams can stay agile and responsive to growing changes, fostering a resilient culture across the organization. Isora provides solutions for information security risk management (ISRM) and third-party-security risk management (TPSRM), helping organizations of all sizes implement complex security frameworks, identify and manage information security risks, and ensure regulatory compliance.
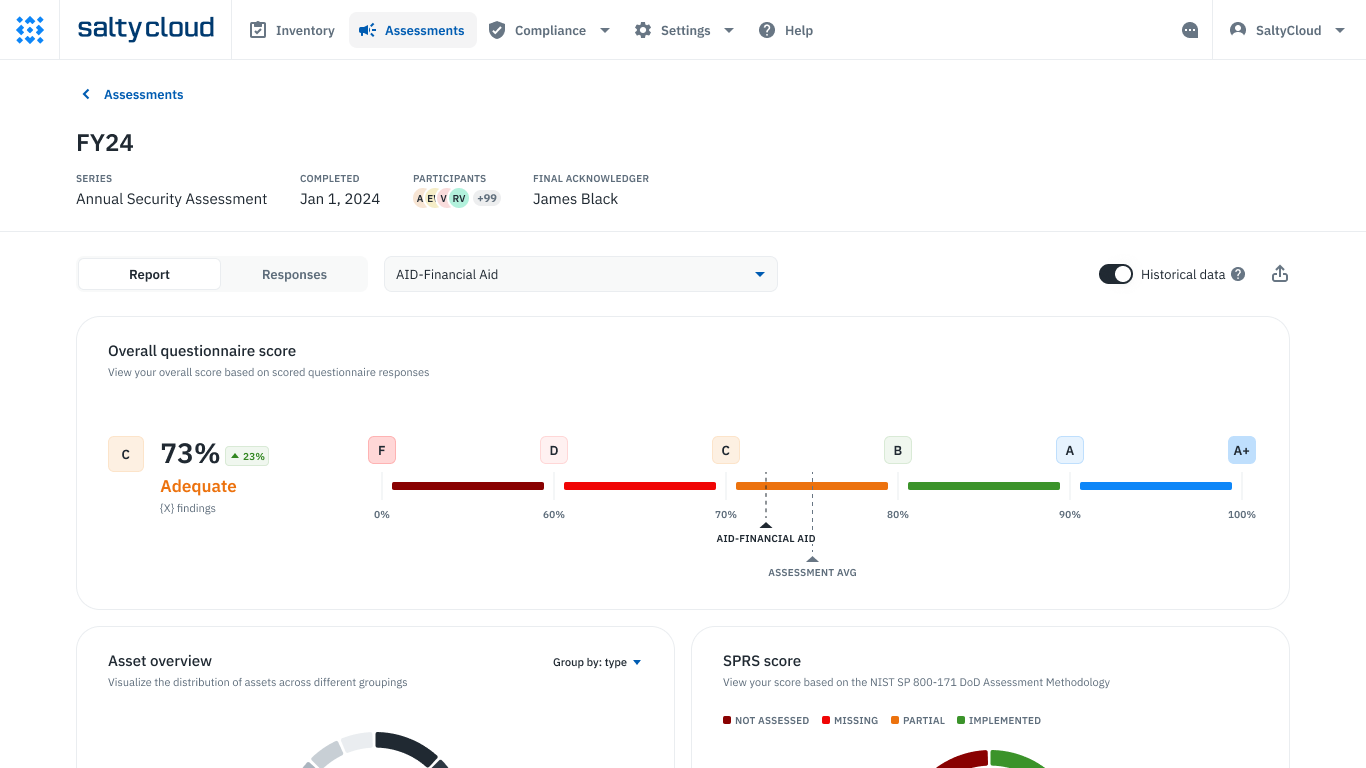
Assessment scorecards and reports in Isora GRC
Conclusion
As we conclude this guide on growing an information security culture, it’s clear that the journey is multifaceted, requiring a blend of robust policy frameworks, dedicated leadership, continuous employee engagement, and the strategic use of technology to achieve this. The right blend of governance, risk, and compliance (GRC) platforms, security awareness training platforms, and anonymous incident reporting systems, bolstered by continuous monitoring solutions, creates an ecosystem where security becomes part of the organizational consciousness.
Remember, an information security culture is not a static entity but a dynamic interplay of behaviors, attitudes, and actions that evolve with the organization. It’s about fostering an environment where vigilance is second nature, and safeguarding information is viewed as a collective responsibility.
Growing and maintaining a culture of information security is a dynamic process that requires commitment, adaptability, and continuous improvement. Organizations that embrace these principles are better equipped to face the cybersecurity challenges of today and tomorrow, ensuring their resilience in an ever-changing digital world.
Looking ahead
Looking ahead, the landscape of information security culture is poised for transformative changes, shaped by technological advancements and emerging threats. Here are some trends to watch:
- Increased focus on human factors: There will be a heightened emphasis on the human factors of cybersecurity, acknowledging that technology is only as strong as the people operating it. This will increase investment in behavioral analytics and the psychology behind security compliance.
- Gamification of training: Security awareness training will likely adopt more gamification elements, making it more engaging and effective. Interactive challenges and simulations will educate and provide employees with a memorable and impactful learning experience.
- Expansion of GRC capabilities: GRC platforms will expand to offer more integrated solutions that manage risk and compliance, provide actionable insights, and foster collaboration across various business units.
Dive into our research-backed resources–from product one pagers and whitepapers, to webinars and more–and unlock the transformative potential of powerfully simple GRC.
Learn More

















 Other Relevant Content
Other Relevant Content