Introduction
Third-party vendor security questionnaires are essential tools in any third-party security risk management (TPSRM) program. Crafted by security experts, these standardized tools help streamline the process of assessing third-party vendors and the security risks they may introduce.
Among the most recognized questionnaires are the Standardized Information Gathering (SIG), Higher Education Cloud Vendor Assessment Toolkit (HECVAT), and Consensus Assessment Initiative Questionnaire (CAIQ). Although it’s an important decision, ultimately, choosing a questionnaire is only the beginning of a long journey toward establishing a mature and resilient Information Security Risk Management (ISRM) program.
This guide from SaltyCloud explores each third-party vendor security questionnaire listed above to help you decide which is the best fit for your organization. Whether you’re looking to save time and resources or just find a tool that aligns with your specific security concerns, understanding the strengths and applications of SIG, HECVAT, and CAIQ is the first step to getting started.
What are third-party vendor security questionnaires?
Third-party vendor security questionnaires are sets of questions designed to evaluate a vendor’s cybersecurity posture. Typically grouped by technical categories, they help organizations identify potential weaknesses that could result in a security incident like a data breach or cyberattack.
Who fills out security questionnaires?
Security questionnaires are filled out by the third-party themselves. Typically, they’re completed by information security professionals. However, it’s not uncommon for salespeople or other roles to contribute.
Why are third-party vendor security questionnaires important?
Security questionnaires are important for internal information security teams because they simplify the process of assessing a third-party vendor’s security measures. By having the third-party vendor self-attest their security practices across various domains, internal security teams can quickly identify potential vulnerabilities and compliance issues while having open and transparent conversations. This process not only aids in the due diligence and risk assessment efforts, but also promotes a culture of security and compliance among all involved parties.
Choosing a questionnaire
The decision can feel overwhelming when it’s time to pick a security questionnaire. Understanding the key features and purposes of each can help guide you to the right choice.
Ultimately, which questionnaire is right for you will depend on your organization’s specific needs, the nature of the data involved, and the vendors you’re assessing.
Let’s break down three major players: SIG, HECVAT, and CAIQ.
SIG
Developed by Shared Assessments, the Standardized Information Gathering (SIG) questionnaire is a structured and comprehensive tool built in Excel for assessing third-party vendor risks. It is particularly valuable for organizations operating in heavily regulated sectors or managing sensitive data. Unlike its alternatives, access to the SIG questionnaire is not free but does include premium tools like an automated Excel template builder and JSON exporter.
The SIG has two versions:
- SIG Core Questionnaire: This version includes 825 questions intended for high-risk vendors.
- SIG Lite Questionnaire: This version offers a condensed format with 150 questions intended for low-risk vendors.
HECVAT
The Higher Education Cloud Vendor Assessment Toolkit (HECVAT) is a comprehensive questionnaire framework built in Excel designed to evaluate the unique set of security risks that higher education institutions face. However, it’s important to note that most questions are universal and can work for any sector.
The HECVAT has four versions:
- HECVAT Triage: This version is an internal questionnaire that helps choose the right kind of HECVAT for your assessments.
- HECVAT Full: This version is for in-depth assessments and includes 265 questions covering 22 categories, including HIPAA and PCI DSS compliance.
- HECVAT Lite: This version offers a condensed format with 62 questions covering 14 categories, ideal for low-risk vendors.
- HECVAT On-Premise: This version is for on-premise solutions with 55 questions across 11 categories, skipping the cloud-centric sections.
CAIQ
The Consensus Assessment Initiative Questionnaire (CAIQ) from the Cloud Security Alliance (CSA) is a free tool built in Excel for documenting security controls in IaaS, PaaS, and SaaS offerings. It’s based on the Cloud Controls Matrix (CCM), which is closely aligned with CSA best practices and is considered the de facto standard for cloud security and privacy.
- CAIQ v4.0: This version includes 261 questions based on the CCM’s cybersecurity framework.
- CAIQ-Lite: This version offers a condensed format with 124 questions.
Which is the best security questionnaire?
The best third-party vendor security questionnaire is one that is specifically tailored to meet your organization’s unique security requirements and the particular context of the vendor being assessed. It should consider the nature of the data the vendor will access and how their services or products integrate with your business operations.
Customizing your questionnaire in this way ensures a detailed and relevant evaluation, targeting not only universal security standards, such as data encryption protocols, access controls, and incident response plans, but also the distinct risks associated with the specific engagement with the vendor, such as potential data sharing vulnerabilities, supply chain risks, or compliance with industry-specific regulations.
The consensus?
When it comes to selecting a security questionnaire, the prevailing wisdom is that there’s no definitive “best” choice applicable to all scenarios, there’s only the “best” for your organization’s unique needs.
Each of the primary tools in use today—CAIQ, HECVAT, and SIG—addresses similar security concerns and spans various security domains, yet they differ in their emphasis, level of detail, and structure. The specific risks and needs of an organization might necessitate a different or more nuanced approach.
Starting with the CAIQ, which is offered at no charge. Crafted predominantly for those assessing cloud service vendors, its straightforward yes/no format is designed to streamline the evaluation process, making it an excellent choice for organizations seeking an efficient yet comprehensive tool for cloud security assessments.
Moving on to the HECVAT. This tool was originally developed with the specific needs of higher education institutions in mind, but has since proven its utility across a broader spectrum, including the public sector. It’s available for free and comes in several versions to accommodate different requirements, including a distinctive on-premise assessment capability. This makes HECVAT particularly well-suited for educational institutions and public sector organizations needing a versatile and sector-specific evaluation tool.
Lastly, the SIG represents the premium tier of security questionnaires, boasting the most extensive collection of questions. This breadth and depth make it the go-to option for a wide array of industries and data types, ideal for organizations that prioritize thoroughness in their security evaluations and are not constrained by budget considerations.
Conducting a third-party security risk assessment
Choosing a third-party vendor security questionnaire is one step in conducting a third-party security risk assessment. In addition to choosing the right questions to include in a questionnaire, it’s equally important to figure out how the process will be managed, especially considering that all three questionnaires rely on Excel. With hundreds of questions across dozens, if not hundreds, of vendors to manage, information security teams need a better solution.
Isora GRC provides a powerful third-party security risk management (TPSRM) solution that helps organizations keep track of their third-party vendors, conduct and manage questionnaire-based assessments, review in-depth vendor reports, and even track risks in a risk register. Isora provides the latest versions of the CAIQ and HECVAT questionnaires and the ability to create a SIG questionnaire if you purchased a license.
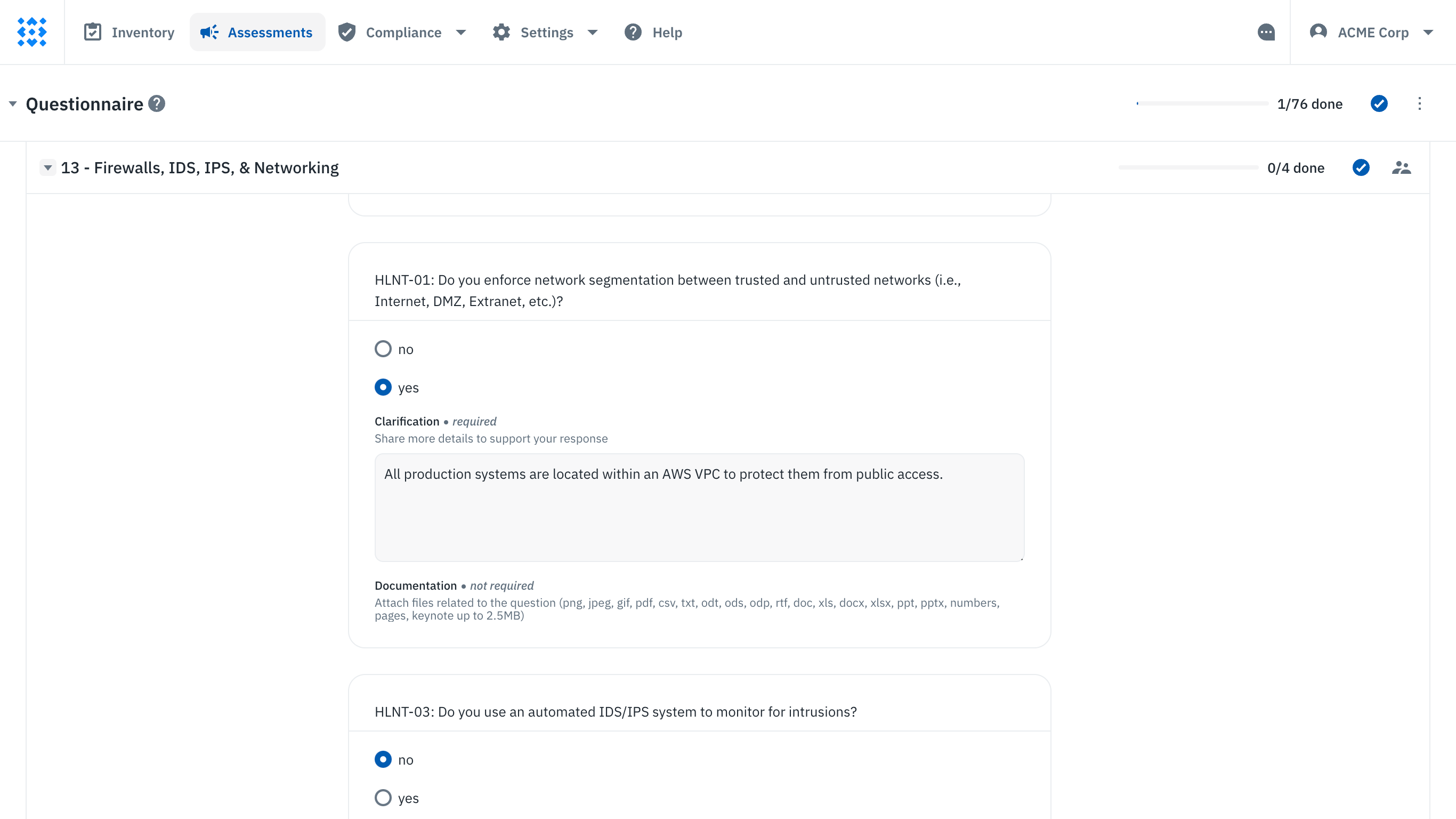
A collaborative HECVAT assessment in Isora GRC
Isora is a collaborative GRC platform that empowers everyone to own risk together, with user-friendly and flexible tools. With Isora, teams can stay agile and responsive to growing changes, fostering a resilient organizational culture.
Conclusion
Selecting a third-party vendor security questionnaire is a critical decision and an important step in your broader third-party security risk management (TPSRM) program. While SIG, HECVAT, and CAIQ each offer valuable features and cater to specific needs, there is no one-size-fits-all solution. Ultimately, which questionnaire you choose should be influenced by factors such as your organization’s requirements, the nature of the data involved, and the specific vendors being assessed. Customization is also key, ensuring that the questionnaire addresses universal security standards and the unique risks associated with each vendor engagement. By selecting the right questionnaire and implementing effective risk management processes alongside it, your organization can improve the transparency and security posture of its third-party vendor ecosystem.
 Cyber Resilience in Higher Education, 2024 Guidebook
Cyber Resilience in Higher Education, 2024 Guidebook





 Table of Contents
Table of Contents

 Other Relevant Content
Other Relevant Content 