 Table of Contents
Table of Contents
- What is Information Security Risk Management (ISRM)?
- Types of Information Security Risks
- Why Information Security Risk Management Is Important
- Benefits of ISRM
- What Are Information Security Frameworks?
- Risk Management Frameworks
- Control Frameworks
- How Risk Management and Control Frameworks Work Together
- Choosing the Right ISRM Framework for Your Business
- How Information Security Risk Management Works in Practice
- How ISRM Works in Action with Isora GRC
- How to Simplify ISRM with IsoraGRC
- Information Security Risk Management FAQs
Most organizations are struggling with information security risk management (ISRM) right now. Today’s digital ecosystems have just gotten too complex for security teams to navigate. It’s just not possible to outmaneuver every security threat, vulnerability, and risk that crops up on the modern attack surface.
Now, data breaches are almost inevitable, annual events for nearly all organizations.
But the stakes have also never been higher for most. With businesses more dependent on information systems and the consequences of a security incident greater than ever, getting ISRM right has never been more important.
This guide explains how to build and maintain a successful ISRM program. It covers the most important frameworks, clear step-by-step instructions, essential tools, and practical best practices. The goal is to make information security risk management more effective at your organization, no matter what that means to you.
So, whether you’re setting up an ISRM program for the first time, modernizing your existing processes, or simply preparing for your next audit, this guide will tell you exactly what to do and how an ISRM tool like Isora GRC can help you do it right.
But first, let’s cover the basics: What is ISRM?
What is Information Security Risk Management (ISRM)?
Information security risk management, or IT risk management, is the structured process of identifying, assessing, and addressing risks to an organization’s information systems, IT assets, and digital infrastructure.
Put simply, ISRM helps organizations find and fix security gaps before they turn into incidents.
The main goals of ISRM are to
- Protect critical information from unauthorized access, exposure, or damage
- Reduce the likelihood and impact of security threats and vulnerabilities
- Maintain business continuity, regulatory compliance, and stakeholder trust
What Makes ISRM Effective?
Managing information security risks effectively takes more than good intentions. Organizations also need a clear strategy, reliable tools, and active participation from teams.
Most successful information security risk management programs are
- Formalized: Clearly defined in documented policies, procedures, and processes (that everyone follows).
- Structured: Based on proven risk management frameworks (like ISO 27005 or NIST RMF) for consistency and repeatability.
- Continuous: Designed for proactive risk management with ongoing risk assessment and monitoring.
- Accountable: Supported by clear roles and responsibilities with measurable incentives for teams.
Next, let’s cover some of the most common types of infosec risks your organization might face and why addressing them is so important.
Types of Information Security Risks
Different information security risks can cause different kinds of damage: financial losses, compliance failures, reputational harm, and more.
Common types of information security risks include:
- Compliance risks: Violations of law, regulations, contracts, or internal policies
- Financial risks: Loss of revenue, unexpected costs, or fraud-related impacts
- System and service risks: Disruptions to IT systems, applications, or infrastructure
- Operational risks: Interruptions to daily work, access, or support processes
- Reputational risks: Damage to brand, public trust, or stakeholder confidence
- Strategic risks: Issues that affect long-term goals or the business’s core mission
Grouping information security risks by type can help security teams clearly communicate what’s at stake. It can help show decision-makers, for instance, that even a single security incident can have wide-ranging, hard-to-measure consequences.
Basically, ISRM gives organizations the tools they need to focus resources on the risks that are most likely to cause the most harm.
Why Information Security Risk Management Is Important
Information security risk management matters because it helps organizations protect their most valuable asset — information — from threats and vulnerabilities.
However, while ISRM has long been fundamental to most security strategies, today’s risk landscape just isn’t what it used to be. It’s far more complex, interconnected, and challenging to secure.
Information security risk management matters because it helps organizations protect information from threats and vulnerabilities.
The Modern Attack Surface
More systems, more vendors, and more sensitive data means the attack surface is larger and risks are harder to manage than ever. But a bigger attack surface also means more sophisticated threats and regulatory requirements as a result. With some form of data breach now inevitable for most organizations, the compounding consequences are beginning to snowball.
The Cost of a Data Breach
In the last two years, 61% of organizations experienced a breach or cybersecurity incident. More than half (55%) had four or more incidents. Today’s data breaches are increasingly common across industries, especially in healthcare, financial services, professional services, and education sectors.
Over half of organizations saw 4+ cyber incidents in the last two years.
But breaches are also more expensive than ever. Up 10% from 2023, the global average cost of a single data breach hit a record $4.88 million in 2024. The average for US companies is nearly twice that at $9.48 million. With the annual cost of cybercrime projected to hit $1.82 trillion by 2028, perhaps it’s unsurprising that cyber risk is the most pressing concern for executives today.
Legacy ISRM Frameworks, Tools, and Workflows
Despite the potentially business-altering fallout following a data breach, most ISRM programs simply haven’t kept up. Only 2% of organizations report having fully implemented a strategic ISRM program. Unfortunately, these programs — often relying on outdated frameworks, manual processes, and reactive approaches — can limit visibility, slow response times, and increase the risk of oversight.
Fortunately, a well-executed ISRM program can help.
Benefits of ISRM
Done right, information security risk management can help your organization identify, manage, and reduce risk more proactively.
An effective ISRM program can help your organization
- Identify risks early, before incidents or downtime.
- Prioritize resources for risk treatments based on real business impact.
- Drive accountability across teams by assigning ownership with clearly defined roles and responsibilities.
- Streamline risk responses by linking risks directly to systems, policies, and controls.
- Improve audit readiness with centralized documentation and reporting.
Let’s dive deeper into the frameworks that underpin effective ISRM programs.
What Are Information Security Frameworks?
Information security frameworks provide the structure needed for truly effective ISRM. These resources, often published by industry standard organizations or regulatory bodies, help guide organizations through various phases of the risk management process.
However, not all information security frameworks do the same thing. Some guide the overall risk management process and methodology, while others offer more specific guidance around security control implementation. Both are essential for ISRM to work.
Understanding the difference between these frameworks (risk management frameworks vs. control frameworks) will be key to selecting the right frameworks for your business.
Risk Management Frameworks
Risk management frameworks provide the structure and methodology for the entire information security risk management process. By helping organizations define how they’ll identify, assess, treat, and monitor risks in advance, these frameworks are essential for creating a consistent, repeatable process across systems, teams, and business units.
Two of the most popular risk management frameworks today are ISO/IEC 27005 and NIST RMF (Risk Management Framework). They follow the same general risk lifecycle but differ in focus, regulatory alignment, and implementation style.
ISO 27005
ISO/IEC 27005 is an international standard for managing information security risk in an ISO/IEC 27001 Information Security Management System (ISMS). It’s widely used across sectors and geographies today and is of particular value for organizations pursuing ISO 27001 certification.
Key characteristics:
- Offers a flexible, adaptable risk assessment methodology
- Designed to scale across different industries, sizes, and maturity levels
- Integrates easily with enterprise risk management (ERM) programs
Best for organizations seeking ISO certification, operating internationally, or needing a globally recognized, business-aligned risk management framework.
NIST RMF
The NIST Risk Management Framework is a seven-step process for integrating risk management across information systems, privacy, and supply chain security. Initially developed for US federal agencies, it’s now widely used by government contractors, critical infrastructure, and heavily regulated industries.
Key characteristics:
- Required for US federal agencies and systems under FISMA
- Aligns with NIST Special Publications like SP 800-37 and SP 800-53
- Includes ongoing control monitoring and organizational risk posture updates
Best for US government agencies, defense contractors, or any organization operating under federal regulations or looking for detailed implementation guidance.
Process Methodology Comparison
| ISO 27005 Steps | NIST RMF Steps | Direct Mapping Explanation | Practical Application |
|---|---|---|---|
| 1. Context establishment
Define criteria for risk evaluation and acceptance |
1. Prepare
Establish risk management activities and priorities. |
Both steps focus on establishing the foundation for risk management by defining criteria, roles, and organizational context. |
|
| 2. Risk identification
Identify assets, threats, and vulnerabilities using event-based and/or asset-based approaches. |
2. Categorize
Classify systems based on impact levels (e.g., High/Moderate/Low). |
Both involve identifying what’s at risk, though NIST focuses more on classifying systems by impact. |
|
| 3. Risk analysis
Determine likelihood and impact using qualitative, quantitative, or semi-quantitative methods. |
3. Select
Choose baseline controls from NIST 800-53 based on system categorization. |
NIST combines analysis with control selection, while ISO 27005 keeps these distinct. |
|
| 4. Risk evaluation
Compare risks against acceptance criteria to prioritize. |
5. Assess
Evaluate if controls are implemented correctly and are addressing requirements. |
Both involve evaluation, but ISO focuses on evaluating risks while NIST focuses on evaluating controls. |
|
| 5. Risk treatment
Choose among mitigation, avoidance, transfer, or acceptance options. |
4. Implement
Deploy selected controls within information systems. |
Both involve implementing actions to address identified risks. |
|
| Part of risk treatment in ISO 27005
Risk acceptance by risk owners. |
6. Authorize
Senior officials approve system operations based on risk. |
ISO 27005 includes authorization as part of risk treatment, while NIST makes it a separate formal step. |
|
| Continuous communication & monitoring
Implied throughout the process. |
7. Monitor
Continuous assessment of controls and organizational risk posture. |
Both emphasize ongoing monitoring, though ISO treats it as integrated throughout rather than a separate final step. |
|
Control Frameworks
Where risk management frameworks help organizations assess and prioritize security risks, control frameworks provide the specific safeguards to address them. These frameworks offer catalogs of technical, administrative, and procedural controls that help teams reduce risk exposure, improve resilience, and meet compliance requirements.
The following are some of the most widely used and trusted control frameworks in information security today.
ISO 27001 Annex A
Annex A of ISO/IEC 27001:2022 outlines 93 security controls grouped across four domains: organizational, people, physical, and technological. Today, most organizations use Annex A to formalize security programs and prove due diligence to external auditors, regulators, and stakeholders.
Key characteristics:
- Direct ties to ISO/IEC 27001 certification requirements
- Includes both strategic and operational measures
- Supports a risk-based, customizable control selection process
Best for organizations seeking ISO 27001 certification, international businesses, or highly-regulated industries looking for a globally recognized security framework.
NIST CSF
The NIST Cybersecurity Framework 2.0 is a voluntary, flexible framework built around five core functions: Identify, Protect, Detect, Respond, and Recover. Initially developed for critical infrastructure, it’s now widely recognized across sectors for its ability to connect security operations to business risk in an outcome-driven way.
Key characteristics:
- Outcome-based structure makes it easy to align security with business objectives
- Frequently used as a baseline or bridge between frameworks
- Regularly updated to reflect emerging threats
Best for critical infrastructure, public utilities, healthcare networks, and mid-to-large enterprises needing a flexible, business-aligned control framework (especially those working with federal or cross-sector partners).
NIST SP 800-53
NIST SP 800-53 is one of the most comprehensive control catalogs available today, covering 20 control families and hundreds of controls. It’s built for federal systems but widely used by organizations requiring a detailed, high-assurance control environment.
Key characteristics:
- Mandatory for US federal agencies and contractors under FISMA
- Includes controls tailored to low, moderate, and high system impact levels
- Maps to ISO/IEC 27001
Best for federal agencies, defense contractors, research institutions, and large enterprises operating in high-assurance or highly regulated environments.
NIST SP 800-171
NIST SP 800-171 defines requirements for protecting controlled unclassified information (CUI) in non-federal environments. Its 110 controls, grouped into 14 families, are focused on confidentiality and built for real-world implementation.
Key characteristics:
- Required for DFARS and CMMC compliance
- Less formal than 800-53
- Often used in federal supply chains
Best for defense industrial base (DIB) contractors, higher education institutions receiving DoD funding, and any non-federal organization handling CUI or working under government contracts.
CIS Controls
The CIS Critical Security Controls offer a prioritized, practical set of security controls to help teams defend against the most common cyber threats. Its controls are grouped into three Implementation Groups (IG1-IG3) based on organizational size, maturity, and resources.
Key characteristics:
- Straightforward starting point for building a risk-informed control set
- Maps to other frameworks (like NIST CSF and ISO 27001)
- Updated frequently based on real-world attack data
Best for small to midsized businesses, IT teams with limited resources, and higher education or local government organizations looking for practical, scalable security controls.
How Risk Management and Control Frameworks Work Together
Risk management frameworks and control frameworks both fall under the broader category of information security frameworks because they typically work together to inform a formalized ISRM program. Because the term ‘framework’ often gets thrown around in conversations about cyber, let’s define what each type actually does.
- Risk management frameworks guide organizations through the process of identifying, assessing, treating, and monitoring information security risks. They outline how to manage risk but don’t specify the exact safeguards to implement.
- Control frameworks provide detailed lists of what to implement — specific security controls, policies, or technical safeguards used to reduce risk.
If risk management frameworks help you understand where risk is, then control frameworks help you respond to it.
The key is that you need both. A risk management framework gives your team structure, and a control framework gives your team tools. Together, they can help your organization prioritize the right risks AND apply the right controls.
Here’s how many organizations combine risk management and control frameworks:
- Start with a risk management framework to identify what could go wrong, how likely it is, and how much it matters.
- Choose security controls from a control framework that match your risk profile and regulatory needs.
- Implement those controls to mitigate high-priority risks and improve your overall security posture.
- Monitor and adapt as your systems, threats, and business requirements change.
Choosing the Right ISRM Framework for Your Business
| Organization Type | Risk Framework | Control Framework | Rationale |
|---|---|---|---|
| Multinational Corporation | ISO 27005 | ISO 27001 Annex A | Global recognition and certification options |
| U.S. Government/Contractor | NIST RMF | NIST SP 800-53 | Alignment with federal requirements |
| Defense Contractor | NIST RMF | NIST SP 800-171 | Specifically designed for CUI protection |
| SMB | ISO 27005/NIST RMF | CIS Controls | Practical implementation with prioritized actions |
| Critical Infrastructure | NIST RMF | NIST CSF | Designed specifically for this sector with flexible implementation |
How Information Security Risk Management Works in Practice
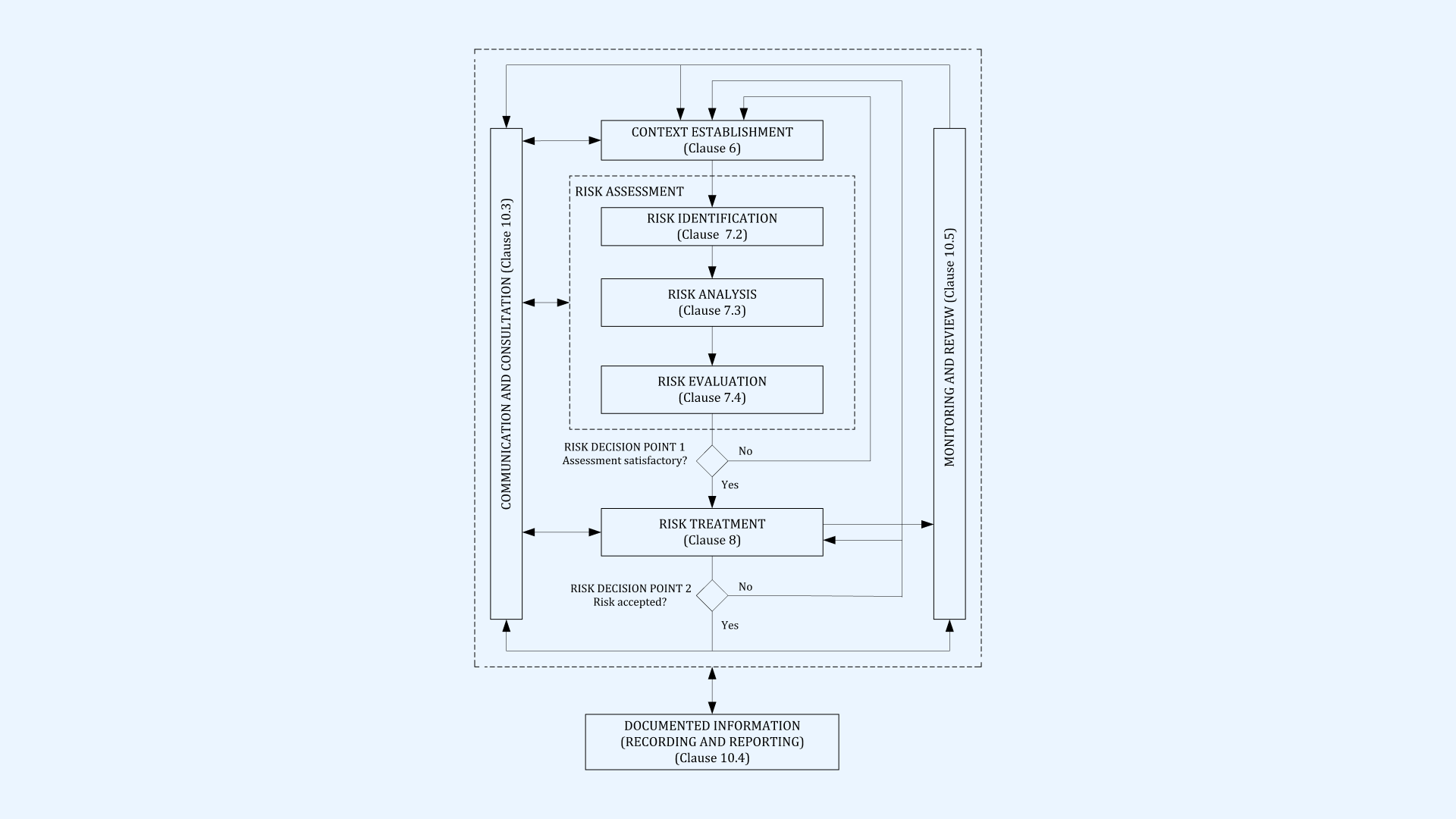
Information security risk management works best when it follows a clear, repeatable process flexible enough to evolve with your systems, vendors, and business priorities.
The steps below outline how ISRM works in practice, from defining your risk landscape to treating and monitoring the threats that matter most. They’re based on the widely recognized ISO/IEC 27005 framework we already covered.
Step 1: Establish the Context
Context establishment lays the foundation for effective risk management by defining exactly what your organization hopes to accomplish, who needs to be involved, and how risk-related decisions will be made. Instead of vague goals like “improve security,” your team will set concrete targets that guide actionable decisions.
Key actions for context establishment include the following:
- Set clear, measurable goals. Identify exactly what your ISRM program should accomplish — whether that’s meeting compliance requirements, reducing third-party risk, or preparing for audits.
- Define your risk evaluation criteria. Clarify how you’ll measure and rank risks, including thresholds for acceptable risk and clear prioritization standards when resources are limited.
- Assign clear ownership. Specify precisely who assesses risk, who owns decision-making responsibilities, who manages critical systems, and who must be kept informed.
- Set explicit boundaries. Clearly document which systems, business units, vendors, and data types your ISRM program covers, and equally important, what’s not in scope.
✅ The result: A documented framework for consistent, transparent risk management decisions — complete with defined objectives, clear scope, explicit risk criteria, stakeholder accountability, and structured reporting.
Challenges with Context Establishment
Common challenges with context establishment are the following:
- Scope creep: Without a clearly documented scope, ISRM boundaries can easily blur, and risk evaluations can quickly derail.
- Unclear ownership: Undefined roles and responsibilities can create confusion, cause missed deadlines, and widen accountability gaps.
- Vague risk criteria: Inconsistent or ambiguous risk evaluation standards can make identifying risks and prioritizing resources difficult across teams.
Fortunately, information security risk management tools can help your organization get more out of its ISRM program from the start.
How IT Risk Management Software Can Help
Modern ISRM platforms like Isora GRC give organizations the tools they need to clearly define and communicate the right context right away.
With Isora, your organization can
- Clarify assessment scope and stakeholder responsibilities so everyone knows exactly who is accountable, responsible, and informed from the outset.
- Structure assessments by business unit, asset, or vendor to keep your ISRM program aligned with existing workflows and organizational structure.
- Customize risk scoring models and thresholds so evaluations directly reflect your organization’s actual risk appetite and strategic goals.
Step 2: Identify Risks
Risk identification means systematically finding and documenting all potential threats and vulnerabilities that could impact your organization’s information assets. The goal is to help your organization understand what it’s protecting, what threats it faces, and precisely where its most significant vulnerabilities are.
ISO/IEC 27005 outlines two common approaches for identifying risks:
- Asset-based approach: Start with specific assets (servers, databases, cloud apps) and identify threats and vulnerabilities unique to each.
- Event-based approach: Start with specific scenarios or incidents (like phishing or ransomware attacks) and identify which assets and vulnerabilities could be targeted.
Key actions for risk identification include the following:
- Build a complete asset inventory. Catalog and classify all critical hardware, software, cloud services, sensitive data, third-party vendors, and user accounts so your team knows exactly what to protect.
- Identify relevant threats. Use internal security data, industry threat intelligence, industry reports, vulnerability disclosures, and regulatory advisories to identify the threats most likely to target your organization.
- Find actual vulnerabilities. Document known weaknesses — misconfigurations, outdated software, missing patches, weak authentication methods, or improper access controls — across your IT systems, networks, applications, processes, and vendor environments.
✅ The result: A complete inventory of risks with direct ties to your critical assets and operations and total visibility for your teams into all the threats, vulnerabilities, and exposures across your organization.
Challenges with Risk Identification
Common challenges during risk identification are:
- Incomplete or outdated asset inventories: Without a clear, centralized inventory, it’s easy to overlook systems or vendors that pose the greatest risks.
- Limited collaboration and visibility: Important insights about threats and vulnerabilities are often missed or misunderstood when departments assess risks in silos.
- Manual data collection: Disconnected spreadsheets, emails, and interviews slow down the information-gathering process, introduce errors, and make risks easier to miss.
How IT Risk Management Software Can Help
Modern ISRM platforms like Isora GRC can transform how your organization gathers, organizes, and reviews risk information.
With Isora, your organization can
- Collect risk data quickly and consistently from teams, system owners, and third-party vendors using built-in questionnaires and surveys — all in one place.
- Centralize your asset and vendor inventory for clear, real-time visibility into exactly which systems, data, and vendors are involved.
- Run collaborative risk assessments across teams to spot security gaps, outdated systems, and compliance issues before they become problems.
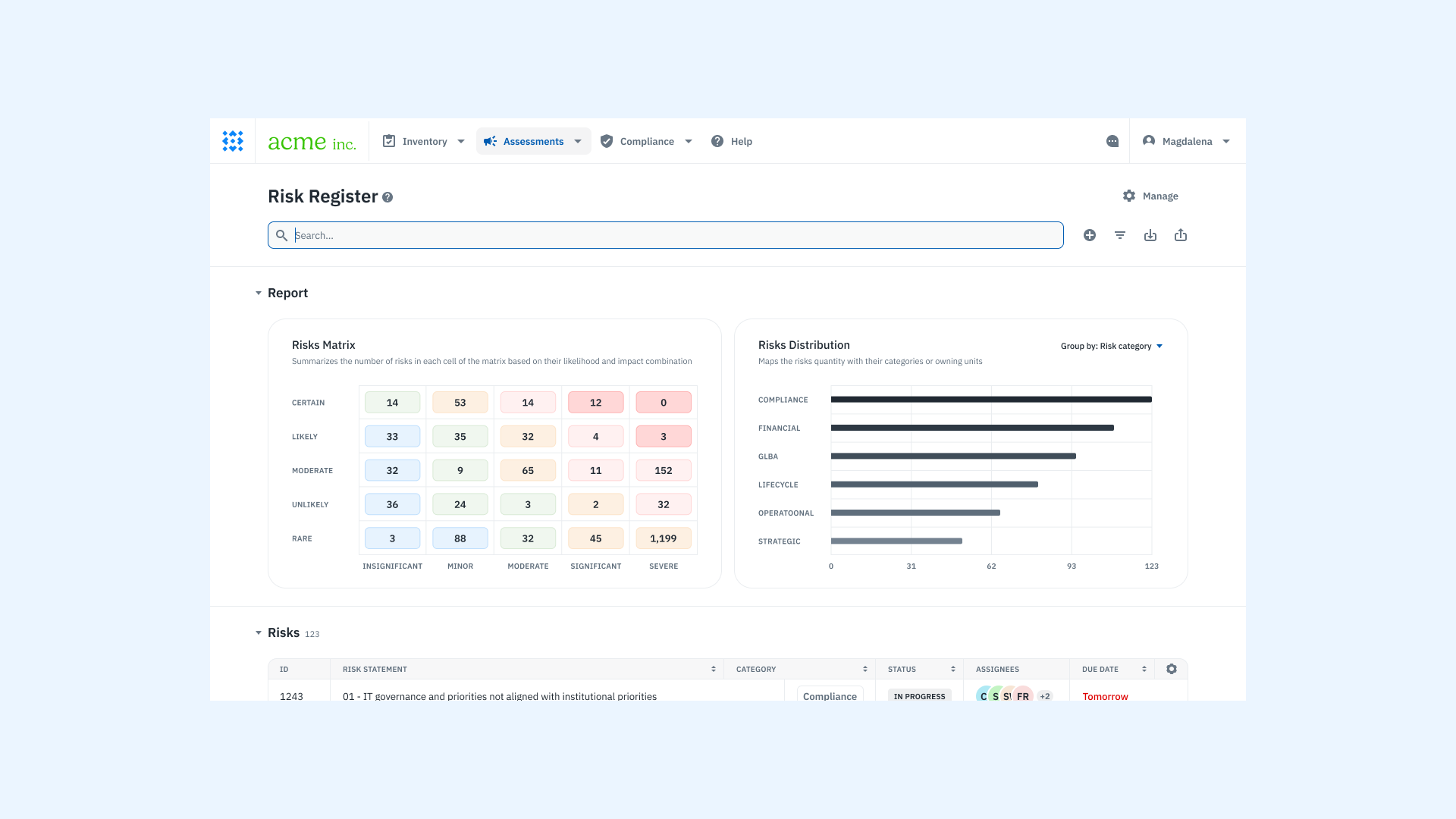
Step 3: Analyze Risks
Risk analysis means evaluating the likelihood of each identified risk occurring and the damage it could cause your organization if it did. This step helps your teams determine which threats and vulnerabilities are truly critical and which can wait.
ISO/IEC 27005 outlines three ways to analyze information security risks:
- Qualitative analysis: Assign risks descriptive ratings (low, medium, or high) to prioritize issues quickly without complex data.
- Quantitative analysis: Use numerical data (e.g., financial losses, downtime hours) for precise, measurable risk calculations.
- Semi-quantitative analysis: Combine qualitative rankings with numerical scoring to balance accuracy and ease-of-use.
Key actions for risk analysis include the following:
- Estimate the likelihood of each risk occurring. Evaluate each threat or vulnerability based on past security incidents, current threat intelligence, vulnerability scans, and industry benchmarks.
- Assess the potential impact. Determine how severely each risk would affect your organization’s data confidentiality, operational integrity, and system availability if it were to occur.
- Calculate overall risk levels. Combine likelihood and impact ratings (qualitatively or quantitatively) to produce clear, actionable risk scores.
✅ The result: A complete list of risks, each assessed by likelihood and potential impact, ready for ranking and prioritization.
Challenges with Risk Analysis
Common challenges with risk analysis are
- Inconsistent risk scoring: Teams that struggle to evaluate likelihood and impact consistently can cause confusion and delays across departments or systems.
- Overly subjective ratings: Without clear scoring criteria, ratings can become subjective or arbitrary, and uncertainty about the true severity or urgency of risks can grow.
- Lack of actionable insights: Quickly translating risk ratings into concrete actions or decisions is hard without standard analysis or clear reporting methods.
How IT Risk Management Software Can Help
Modern ISRM solutions like Isora GRC can give your organization the structured, standardized methods to analyze risks more effectively.
With Isora, your organization can:
- Score risks consistently with configurable fields in a centralized risk register that make it easy for teams to understand the severity of each risk based on evidence.
- Make prioritization decisions more transparent and defensible by clearly connecting each risk to its likelihood, potential impact, and supporting evidence.
- Automatically measure assessment results with built-in reports and scorecards that help teams track progress and spot the risks that need attention first.
Step 4: Evaluate Risks
Risk evaluation is where your team compares the risks it has analyzed against clearly defined criteria to determine exactly which ones require attention. In this step, you’ll prioritize efforts based on your organization’s documented risk appetite and acceptance thresholds, clearly distinguishing:
- Risks that exceed acceptance levels (immediate action required).
- Risks that fall within acceptable levels (no immediate action required).
Key actions for risk evaluation include:
- Compare risks against risk criteria. Assess each risk’s severity against your organization’s documented risk tolerance to distinguish acceptable risks from those needing action.
- Prioritize critical risks. Document and highlight risks that exceed acceptable levels so your team knows which issues need immediate attention and resources.
- Document risk acceptance decisions. Record the rationale behind accepting certain risks, including evidence, justification, and approval to support transparent, informed decision-making.
✅ The result: A prioritized list of risks that clearly defines which issues to address first, which to defer, and which to formally accept based on well-defined and documented criteria.
Challenges with Risk Evaluation
Common challenges with risk evaluation are
- Unclear risk thresholds: Without explicit criteria or guidelines, teams can struggle to know which risks to accept, escalate, or mitigate first.
- Inconsistent documentation: Decisions around accepted or prioritized risks that lack proper documentation can create confusion, compliance gaps, and audit challenges.
- Manual escalation processes: Delays, miscommunication, and oversights are common byproducts of manual or informal methods for flagging and escalating high-priority risks.
How IT Risk Management Software Can Help
Isora GRC can give your team the structured, transparent approach it needs to prioritize risks and track decisions.
With Isora, your organization can
- Automatically flag high-risk items in a centralized risk register to highlight critical risks based on scoring thresholds and criteria unique to your organization.
- Effortlessly track exceptions using an integrated risk exception register that documents and maintains records of accepted risks, rationales, and approval workflows.
- Apply your risk acceptance criteria automatically, with built-in scoring logic and auto-escalation capabilities for defensible decision-making.
Step 5: Treat Risks
Risk treatment is about taking targeted actions to address the risks your organization has identified as top priorities. It involves choosing the most effective way to handle each risk, documenting your approach, and implementing controls that align with your organization’s objectives and available resources.
ISO/IEC 27005 outlines four risk treatment strategies:
- Risk mitigation: Reducing the likelihood or impact of risks by implementing targeted controls like endpoint protection, access management, or employee training programs.
- Risk avoidance: Removing the risk entirely by discontinuing services or changing processes that introduce unacceptable exposure.
- Risk transfer: Shifting some or all responsibility to a third party through measures like cyber insurance or contractual agreements with vendors.
- Risk acceptance: Acknowledging and formally documenting any residual risks that your organization chooses not to address immediately, provided they fall within acceptable risk thresholds.
Key actions for risk treatment include the following:
- Select and document appropriate controls. Choose controls aligned to industry frameworks (like ISO/IEC 27001 Annex A, NIST SP 800-53, or CIS Controls) to address risks.
- Implement selected safeguards. Deploy technical, administrative, and operational measures designed to mitigate, avoid, or transfer risks effectively.
- Track and document treatment plans. Keep detailed records of your chosen strategies, assigned responsibilities, implementation timelines, and expected outcomes for clarity, compliance, and audit readiness.
✅ The result: An actionable risk treatment plan that clearly defines how each risk will be addressed, including timelines, ownership, selected controls, and documented rationales for accepted risks.
Challenges with Risk Treatment
Common challenges with risk treatment are
- Unclear ownership and accountability: Without clearly assigned roles and responsibilities, risk mitigation tasks can stall, vulnerabilities can go unaddressed, and controls can be delayed or ineffective.
- Fragmented documentation and tracking: Tracking risk treatment plans and controls across separate systems or spreadsheets makes real-time visibility and continuous monitoring nearly impossible.
- Inconsistent evaluation and follow-up: Organizations often struggle to determine the effectiveness of controls without structured assessments to prove whether treatments actually reduce risk.
How IT Risk Management Software Can Help
Modern ISRM platforms like Isora GRC can give your organization the structure and visibility it needs to implement, track, and manage risk treatments effectively.
With Isora, your organization can
- Centrally assign and manage risk treatment tasks, delegate responsibilities, define timelines, and document treatment plans so security teams can stay on track and stakeholders can track progress.
- Link risk treatments to assets, risks, and business units for more transparent and organized records, more effective oversight, simpler compliance reporting, and better security insights for your teams.
- Automatically trigger follow-up risk assessments to measure control effectiveness with automated workflows that validate whether your security measures are actually reducing risk levels.
How ISRM Works in Action with Isora GRC
Imagine a national healthcare organization responsible for protecting patient records, clinical systems, and sensitive third-party data.
To align with frameworks like NIST CSF and improve visibility into its security posture, the organization uses Isora GRC to assess internal departments and vendors, identify control gaps, and manage risk across its ecosystem.
Here’s how this team might apply ISO 27005 and Isora GRC in practice:
- Establish Context: The security team defines the scope of its assessment using Isora’s centralized inventory—targeting clinical systems, administrative units, and key third-party vendors responsible for handling regulated data.
- Identify Risks: With prebuilt and custom questionnaires, the team assesses control maturity across NIST domains like access control, configuration management, and incident response. Responses are tied to assets and business units.
- Analyze Risks: Isora’s reports and scorecards automatically score responses and flag gaps—such as missing MFA on critical systems or lack of endpoint protection among vendors—highlighting areas with high potential impact.
- Evaluate Risks: Risks are published to a centralized risk register where they can be compared against the organization’s documented tolerance levels. High-likelihood, high-impact gaps—especially in areas tied to sensitive data—are prioritized for remediation.
- Treat Risks: The team assigns remediation tasks and tracks exceptions. That includes policy updates, technical fixes, or submitted justifications when risk is accepted.
- Monitor & Communicate: With Isora’s continuous assessments and reporting tools, the team can track remediation progress, demonstrate control maturity across units, and generate audit-ready reports—making it easy to keep leadership informed and prove the impact of security initiatives.
How to Simplify ISRM with IsoraGRC
Managing information security risk shouldn’t require stitching together spreadsheets, chasing down responses, or guessing who owns what. But for many security teams, that’s still the reality—manual processes, scattered systems, and limited visibility.
Isora GRC brings structure to the entire ISRM workflow. From assessments and inventories to exception tracking and remediation, every task is centralized and assigned—so your team can spend less time managing the process and more time managing the risk.
No disconnected tools. No guesswork. Just a platform built to help security teams work smarter at scale.

Information Security Risk Management FAQs
Still have questions about information security risk management? This FAQ section answers common questions about building, implementing, and managing an effective ISRM program.
Who is responsible for managing security risks?
Managing information security risk is a shared responsibility. Security teams usually lead the process, but system owners, department leads, and executive stakeholders all play a role. Risk decisions — like whether to mitigate, accept, or escalate — should be made by the people who understand the impact and have the authority to act.
How do you identify information security risks?
Security teams identify information security risks by assessing the controls, systems, and processes in place across departments, vendors, and assets. This typically involves issuing structured assessments aligned to frameworks like NIST CSF or 800-53, collecting evidence and documentation, and evaluating control maturity.
What is an IT risk assessment?
An IT risk assessment is the structured process used to identify, analyze, and evaluate security risks across their technology environment. The goal is to clearly determine which threats and vulnerabilities could realistically affect your organization’s systems, data, or operations, and how severe that impact could be. Risk assessments give security teams a clear view of their highest-priority risks, guiding informed decisions about how and when to address them.
How do you perform an IT risk assessment?
Performing an IT risk assessment starts by clearly defining its scope—documenting exactly which systems, applications, or business processes you’re reviewing.
Then, your team collects relevant risk data through internal questionnaires, stakeholder interviews, and security documentation.
Next, you’ll systematically identify threats and vulnerabilities, analyze how likely they are to occur, and assess the potential impact on your organization’s confidentiality, integrity, and availability.
Finally, you’ll assign clear, consistent risk ratings to guide what happens next.
How do you prioritize risks in ISRM?
Risk prioritization is when you compare each risk’s likelihood and potential impact against clear criteria you’ve already defined. The highest priority goes to risks that are most likely to happen and could cause significant damage, like compliance failures, costly downtime, or reputational harm. This makes it easy for your organization to see which risks need immediate action, which can wait, and which are acceptable for now.
How do you manage IT exceptions?
Managing IT exceptions involves clearly documenting risks your organization chooses to accept, at least temporarily, instead of immediately addressing them. For each exception, you’ll need to explain why accepting the risk makes sense right now, who approved it, and what measures you’ve put in place to minimize potential impacts. You’ll also need to set a clear timeline to revisit the exception to ensure it’s still appropriate as your business environment changes.
Dive into our research-backed resources–from product one pagers and whitepapers, to webinars and more–and unlock the transformative potential of powerfully simple GRC.
Learn More


















 Other Relevant Content
Other Relevant Content