 Table of Contents
Table of Contents
- What is the GLBA Safeguards Rule?
- What is a GLBA Safeguards Rule Risk Assessment?
- GLBA Safeguards Rule Risk Assessment Checklist
- What’s Next After a GLBA Assessment?
- Beyond the Risk Assessment
- Final Thoughts on the GLBA Safeguards Rule Risk Assessment
-
FAQ: GLBA Safeguards Rule Risk Assessment
- What are the GLBA Safeguard Rule Requirements?
- Who must comply with the GLBA Safeguards Rule?
- Who enforces compliance with the GLBA Safeguards Rule?
- What happens if you don’t comply with the GLBA Safeguards Rule?
- How often should we conduct a GLBA risk assessment?
- Why is Compliance with the GLBA Safeguards Rule Important?
- Why are GLBA Safeguards Rule risk assessments so challenging?
- What’s the most common mistake during a risk assessment?
- Do we need special software for a GLBA risk assessment?
A GLBA Safeguards Rule risk assessment is a formal, structured process for organizations to identify, assess, and address information security risks in compliance with the Gramm-Leach-Bliley Act (GLBA).
A federal law requiring financial institutions to protect consumer financial information, the GLBA organizes its compliance requirements under three “rules”: the Privacy Rule, the Safeguards Rule, and the Pretexting Rule. Because it calls for ongoing efforts to design, implement, and maintain an information security program, the Safeguards Rule will likely be the biggest compliance lift for most institutions.
And that’s why we created this GLBA Safeguards Rule risk assessment guide and checklist just for you. 💚
Here’s a quick overview of the GLBA Safeguards Rule risk assessment process:
- Step 1: Define the scope.
- Step 2: Select a security framework.
- Step 4: Launch the assessment.
- Step 5: Collect details and evidence.
Obviously, this is a dramatic oversimplification of what is typically a very complex, nuanced process. Keep reading for a much closer look at the Safeguard Rule’s risk assessment process and our recommendations for conducting a great assessment.
Note: We already covered the three GLBA rules in our complete GLBA guide. But the Safeguards Rule is where the regulation gets extra specific about information security requirements, so we’re giving it some extra attention.
So, what is the GLBA Safeguards Rule? What is a GLBA Safeguards Rule risk assessment? And how do organizations conduct one?
Don’t worry, friend—we’ve got you covered. Here, we’ll break down everything you need to know about conducting a GLBA Safeguards Rule risk assessment: what it is, why it matters, and steps to do it right.
So whether you’re doing it for the first time or simply looking for a better workflow, you’re in the right place. ‘Cause we’re about to drop a knowledge bomb on you.
Boom! Let’s do this. 🧠💣💥
What is GLBA?
GLBA is an acronym for the Gramm-Leach-Bliley Act, a U.S. federal law that sets forth requirements for financial institutions to protect the privacy, confidentiality, and security of consumer financial information.
Read our complete GLBA guide for more.
What is the GLBA Safeguards Rule?
The GLBA Safeguards Rule (16 CFR 314.4) is a federal law requiring financial institutions to develop, implement, and maintain an information security program. Known formally as the Standards for Safeguarding Customer Information, it introduces administrative, technical, and physical safeguards for financial institutions to protect and secure customer information.
An important part of the Gramm-Leach-Bliley Act (1999) the Safeguards Rule was issued by the Federal Trade Commission (FTC) in 2001 and became enforceable in 2003. The most significant GLBA Safeguards Rule update in 2021 introduced mandatory risk assessments and reporting requirements for financial institutions with more than 5,000 customer records. It also introduced eight new cybersecurity requirements for GLBA compliance and made GLBA compliance enforceable for Title IV higher education institutions.
The Rule was updated again in 2023 with a breach notification requirement for financial institutions involving unauthorized access to the unencrypted information of at least 500 consumers and a Safeguards Rule Security Event Reporting Form for submissions.
Today, the Safeguards Rule is about making sure that financial institutions take reasonable steps to secure customer information. But it doesn’t simply suggest that organizations improve their infosec programs. It gives them specific requirements to do so.
Now, let’s take a closer look at one of the Safeguard Rule’s most daunting requirements: the risk assessment.
What is a GLBA Safeguards Rule Risk Assessment?
A GLBA Safeguards Rule risk assessment is a mandatory requirement for financial institutions to identify, evaluate, and address information security risks to consumer financial data.
More specifically, the Safeguard Rule states in its second requirement, 16 CFR 314.4(b), that financial institutions must base their information security risk programs on…
“A risk assessment that identifies reasonably foreseeable internal and external risks to the security, confidentiality, and integrity of customer information that could result in the unauthorized disclosure, misuse, alteration, destruction, or other compromise of such information, and assesses the sufficiency of any safeguards in place to control these risks.”
It also stipulates that the risk assessment must be written and performed periodically and include criteria for evaluating and categorizing security risks, criteria for assessing information systems and customer information, and requirements for addressing risks.
Essentially, the goal of a Safeguards Rule risk assessment is to help institutions answer the question, “How well are we protecting our customer’s sensitive financial information from cyber threats?” While this might sound simple enough, the actual process of conducting a Safeguards Rule risk assessment is anything but.
The bottom line is that conducting a GLBA risk assessment isn’t just about answering a few questions. It’s about evaluating your entire security program, managing third-party compliance, and maintaining detailed records for auditors—all at once. And without the right tools or processes in place, it can quickly spiral into chaos.
Conducting a GLBA risk assessment isn’t just about answering a few questions. It’s about evaluating your entire security program, managing third-party compliance, and maintaining detailed records for auditors—all at once.
GLBA Safeguards Rule Risk Assessment Checklist
Safeguards Rule risk assessments are a mandatory, multi-step requirement for financial institutions to identify, assess, and mitigate security risks in compliance with the GLBA.
Although mandatory, it can be hard for financial institutions to know where to begin with GLBA compliance, so we created this step-by-step checklist to help get you started with a risk assessment process that’s structured, actionable, and repeatable.
Follow these steps to identify security risks, protect your customers, and stay compliant—without the guesswork.
Step 1: Define the Scope
The first step of a GLBA Safeguards Rule risk assessment is to define the scope—the people, business units, assets, and vendors you’ll analyze. Basically, you need to define what it is you’re evaluating before you can actually start the assessment process.
Here’s how to define the scope of your risk assessment:
- Map out customer financial data by locating where it’s stored, processed, and transmitted on your systems, in the cloud, or with third-party vendors—and writing it down.
- List all users with access, including everyone with access to sensitive data—employees, partners, service providers, etc.—and decide whether their privileges are appropriate.
- Narrow your focus to GLBA—the departments, IT systems, and vendors handling consumer financial information subject to GLBA compliance.
Why this step matters: Without clear guidelines, your team might waste precious time and resources assessing risks for systems that don’t even interact with sensitive data.
But scoping a risk assessment isn’t easy, especially when your teams work in spreadsheets and even more so without a current IT asset inventory. If you haven’t already, this is the opportunity to update your inventory…before you get stuck in the weeds. 👀
Not sure where to begin with IT asset management? Fortunately, there are several industry-standard guides available to help.
Here are some common IT asset management frameworks:
- NIST 1800-5: Offers a modular approach for identifying, tracking, and securing hardware and software systems.
- IEC 19770-1:2017: Defines best practices for tracking, controlling, and optimizing hardware and software throughout their lifecycle.
- CMMC Assessment Scope – Level 2: Defines the scope for a Cybersecurity Maturity Model Certification (CMMC) assessment and classifies assets into categories, including “Controlled Unclassified Information (CUI).”
- CIS Critical Security Controls v8: Establishes best practices for inventorying and managing enterprise assets, ensuring only authorized devices are tracked, controlled, and secured.
💡Tip: A tool with a centralized inventory management dashboard like Isora GRC can help teams manage GLBA-covered assets, apps, and vendors all in one place.
With Isora, you can track risk owners, data classifications, categories, deployments, notes, and more. Simply add your inventory manually or upload it automatically—and let Isora do the rest.
Step 2: Select a Security Framework
Next comes deciding which framework to use for your security risk assessment. But first, let us clarify: the Safeguards Rule lists the controls and requirements for GLBA compliance but does not prescribe a particular security framework. Instead, it leaves the decision up to organizations.
Most organizations align their information security program with an industry-recognized, standardized framework. Combining a mix of policies, procedures, and technical measures, these frameworks offer guidance intended to help organizations implement and maintain security controls effective enough to uphold the integrity, confidentiality, and availability (CIA) of data.
In some rare cases, organizations might try to create their own security framework—but they are the exception, not the rule. Standardized frameworks are industry-recognized for a reason: they’re effective, and they’re easy enough for most organizations to implement. Our take? Go with what works well for others. (If it ain’t broke, don’t fix it.)
Here are some common risk assessment frameworks:
- NIST 800-53: Establishes security and privacy controls for U.S. federal information systems, helping agencies and contractors safeguard sensitive data, manage risk, and ensure compliance.
- NIST CSF: A flexible, risk-based framework that helps organizations improve cybersecurity posture through five core functions—Identify, Protect, Detect, Respond, and Recover.
- NIST 800-171: Defines security requirements for protecting controlled unclassified information (CUI) in non-federal systems, focusing on access control, incident response, and risk management.
- ISO/IEC 27001: Guidelines for building a structured, risk-based information security management system (ISMS) with policies, continuous monitoring, and risk mitigation strategies that protect data CIA.
- SOC2: Evaluates an organization’s ability to securely manage customer data based on five trust principles: security, availability, processing integrity, confidentiality, and privacy.
- CIS Critical Security Controls: Outlines fundamental security best practices, including access controls, asset management, continuous monitoring, and secure system configurations, to mitigate cyber threats.
Why this step matters: A structured, standardized risk management framework can help you identify security risks and protect your organization and its customers more effectively and with less effort. Why reinvent the wheel when there’s already a host of well-established, recognized, tried, and true frameworks at your fingertips?
Which framework your institution chooses will ultimately depend on the size, complexity, and state of your existing information security program. But at the end of the day, the best framework will be the one your team can actually implement and maintain—because a compliance plan that just sits on the shelf doesn’t do anyone any good.
The best framework will be the one your team can actually implement and maintain.
Step 3: Create a Self-Assessment Questionnaire (SAQ)
After selecting a framework, it’s time to create a self-assessment questionnaire to collect details about security practices from different teams across your institution.
Also called a compliance questionnaire or a control self-assessment (CSA), an SAQ is a structured set of questions designed to help organizations evaluate internal processes, risks, or compliance against predefined controls. It’s a simple yet effective way to measure where your organization’s security posture currently stands and determine what steps to take for improvement.
SAQs should ask questions about the following:
- Access Controls: Who can access sensitive financial data? Do they have the appropriate permissions? Do you have multi-factor authentication (MFA) and least-privilege policies in place to prevent unauthorized access?
- Encryption and Data Protection: Do you encrypt financial data in transit and at rest? What safeguards do you have to prevent unauthorized access or exposure? Do you securely manage encryption keys?
- Incident Response: Do you have a formal incident response plan? How quickly can your security team detect, contain, and report a data breach? Can your employees recognize and escalate security incidents?
- Third-party Vendor Risk Management: Do vendors handling sensitive financial information follow security standards? Have they conducted a security assessment? Do you have contracts stipulating strong security controls?
Why this step matters: Asking the people who actually work for your company questions about security processes—and hoping they answer honestly—is just about the only realistic way to uncover security and compliance gaps. But it also takes some finesse.
Ideally, SAQ Safeguards Rule questions should be detailed enough to help you get a clear picture of the risk landscape without overwhelming your respondents. At the same time, the more evidence you can collect, the better—it’s tangible proof that you take risk management efforts seriously. Striking the right balance between these opposing truths will be key for a successful SAQ.
Key elements of a GLBA Security Rule SAQ include the following:
- Control Questions: Write questions with enough context to extract detailed, meaningful answers from respondents.
- Question Categories: Organize questions by security domains (e.g., Access Controls, Vulnerability Management, etc.) to evaluate strengths and weaknesses in specific areas.
- Question Weights: Use a weighted scale to rank the importance of different security controls and prioritize high-risk areas first.
- Answer Choices: Structure questions in two primary formats—binary (yes/no) for straightforward answers and scaled questions for more nuanced responses.
- Impact Multipliers: Apply these to significant answer choices to make sure critical, high-risks get attention first.
💡Tip: Not sure how to create scaled questions? We recommend the Capability Maturity Model (CMM) for additional guidance on using a graded scale (like 1 to 5) to evaluate security controls.
Step 4: Launch the Risk Assessment
Finally, it’s time to kick off the risk assessment process. Here, you’ll need to consider some logistics—how will you involve the right people and make sure responses come back complete, accurate, and on time? Setting clear expectations ahead of time can help avoid issues like half-finished SAQs, missing evidence, or vague answers.
How to launch a GLBA Safeguards Rule risk assessment:
- Distribute it to the right teams, making sure department heads, IT, security, and third-party vendors know who needs to respond and what’s expected.
- Set deadlines upfront to avoid a risk assessment with no due date. Give teams a clear timeline for completion, with plenty of reminders along the way.
- Explain the evidence requirements so participants know they’ll need to back up their responses with documentation like access logs, security policies, or incident response records.
Why this step matters: A successful launch sets the tone for the rest of the risk assessment process. If you don’t communicate your expectations clearly, you’ll likely spend more time chasing responses than actually assessing risks. But this step can also be easier said than done—especially when SAQs get lost in email threads and spreadsheets.
With GLBA compliance software like Isora GRC, on the other hand, institutions can easily organize all assessment details and SAQ questions into a single, collaborative survey. Simply select the units, people, and assets to assess, choose a questionnaire template and provide instructions, and set a due date for automated notifications.
Isora’s GLBA assessment dashboard lets you track assessment statuses, view details, and documentation, and generate scorecards and risk reports upon completion.
💡Tip: Distribute, track, and manage SAQs all in one place with Isora’s unified assessment management dashboard—and stop following up with every single SAQ participant.
Step 5: Collect Details and Evidence
A GLBA Safeguards Rule risk assessment is only as good as the evidence it collects. Because asking teams if they have certain controls in place is one thing. Getting actual proof those controls exist is another. Ultimately, this step is about verifying answers and collecting supporting documentation that confirms your compliance efforts aren’t just theoretical.
Asking teams if they have certain controls in place is one thing. Getting actual proof those controls exist is another.
Even if you haven’t done this process before, you can probably imagine how quickly this step can spiral out of control. Simply collecting all the documentation for an internal security risk assessment can take weeks (if not months) IF everything stays on track.
Remember that bit about setting a deadline? This is where you’ll start to see why it was so important.
Collect the following details, evidence, and documentation:
- Security Policies: Documented policies for access control, encryption, vendor security, and more.
- Access Logs and Permissions Reports: Proof that only authorized users can access sensitive financial data.
- Encryption Configurations: Screenshots or system settings showing encryption in transit and at rest.
- Incident Response Plans: Written procedures outlining how your team detects, reports, and responds to security incidents.
- Third-Party Security Assessments: Vendor security reports or audit results to verify regulatory compliance.
💡Tip: Auditors LOVE documentation, so the more, the better. Store your GLBA compliance evidence in a centralized inventory to keep everything organized in one place where everyone can see it.
Why this step is important: Without solid evidence, a risk assessment is just a collection of yes/no answers—which won’t hold up under an audit OR a security incident. The more documentation you have, the stronger your security posture will be.
💡Tip: If your security documents are still scattered across emails, shared drives, and filing cabinets—it’s 2025, and there’s a better way. With Isora GRC, survey participants can attach documents directly to their SAQ responses, and Isora will store them for audit readiness.
Step 6: Analyze, Identify, and Evaluate the Risks
Now comes the moment of truth: with all the SAQ responses and evidence collected, it’s time to dig into the results of your GLBA Safeguards Rule risk assessment.
To be blunt, simply scanning the answers won’t cut it here. Your information security team needs to critically assess each and every response, cross-check the evidence, identify security gaps, and pinpoint exactly where vulnerabilities are hiding. Then, they need to translate that raw data into actionable steps that are simple enough for the non-security experts at your organization to understand.
How to analyze GLBA Safeguards Rule risk assessment results:
- Look for conflicting, incomplete, or inconsistent responses by asking questions like, “Do the SAQ answers match the evidence?” If a team claims, “Yes, we encrypt all sensitive data,” for example, but submits no encryption documentation, that’s a big red flag that needs close examination.
- Identify missing or weak security controls—some of which are obvious, like a missing MFA policy, while others need a closer look. Pay close attention to common high-risk gaps like excessive user access permissions, unpatched software, outdated policies, or lack of monitoring capabilities.
- Rank risks based on severity because some issues simply pose a bigger threat than others. Prioritize which risks to address based on impact and likelihood—high-risk gaps should be first.
- Assign risk owners to track remediation efforts makes real people accountable which can increase the chances for a favorable outcome. Remember, a risk without an owner is a risk that won’t get fixed.
- Document everything with a detailed record of your findings, including all identified risks ranked by severity, supporting evidence for each finding, risk owners and mitigation steps, remediation timelines, and follow-up assessments.
Why this step matters: Congratulations! 🎉You have officially reached the penultimate step of the GLBA Safeguards Rule risk assessment process. Rest assured, knowing its success ultimately hinges on how well you’ve laid the foundation with every step leading up to it. No pressure!
If you’ve followed our GLBA risk assessment checklist to a T so far, then you’re probably in pretty good shape. Now, it’s up to you to identify the biggest risks, prioritize what needs the most immediate attention, and recommend actionable steps to improve security controls and reduce risk.
💡Tip: Log risks, assign owners, track remediation efforts, and set deadlines so nothing falls through the cracks with collaborative risk management tools from Isora GRC.
What’s Next After a GLBA Assessment?
Completing a GLBA Safeguards Rule risk assessment is a big accomplishment—but it’s only the beginning. So what’s next?
Here’s what to do after a GLBA Safeguards Rule risk assessment.
Log Risks in a Risk Register
A risk register is your master log of everything you discovered during the assessment—the good, the bad, and the ugly.
Here’s how to log risks the right way:
- Write clear, descriptive risk entries. For example, don’t just say, “Weak encryption.” Be specific: “Customer data is encrypted with outdated protocols.”
- Assign risk owners immediately, selecting a specific person or team with a clear deadline.
- Classify and prioritize risks by severity, impact, and likelihood. Use simple categories like Critical, High, Medium, and Low to determine what to do first.
- Document mitigation plans for each risk, listing the proposed solution, the risk owner, the expected timeline, and any additional resources.
💡Tip: Isora GRC lets you publish risk assessment findings directly into its centralized risk register, assign risk owners, and track risk remediation progress in real time.
Make it a Continuous Process
Conducting regular, ongoing GLBA Safeguards Rule risk assessments can help you stay ahead of risks and demonstrate that you take security seriously to regulators. Plus, threats evolve, data environments change, and compliance requirements get updated.
Here’s how to make your risk assessment process continuous:
- Schedule regular follow-up assessments with at least one per year, but more frequently—like quarterly SAQs for high-risk systems—to detect problems sooner.
- Reuse historical data so you don’t have to start from scratch every time. Use the previous year’s findings as a baseline to track trends, recurring issues, and improvements.
- Update the SAQ regularly, reviewing your questions to reflect new risks (like AI/ML systems) or process changes.
- Monitor third-party vendors’ security reports, SOC 2 audits, and HECVAT results to verify ongoing compliance.
💡Tip: Isora makes follow-up assessments easy. In Isora, teams can pull forward historical responses and evidence and track assessment results over time to spot recurring problems or improvement patterns.
Prepare for Audits and Demonstrate Compliance
Eventually, regulators will want proof of compliance—and when that day comes, you’ll want to be ready to preset your risk assessment results in a clear, organized, and accessible way.
How to prepare for GLBA audits:
- Organize your documentation because auditors need more than just your final report. Be sure to include completed SAQ responses (with supporting evidence), risk register entries (with risk owners and remediation plans), data flow diagrams (showing where customer data is stored and transmitted), and security policies and procedures (especially access control, encryption, and incident response).
- Review regulatory guidance to stay current. Check out resources like the OCC’s examination procedures for federally regulated financial institutions, the ED’s FSA Cybersecurity Compliance Requirements for higher ed institutions handling student financial aid, and the FTC Safeguards Rule Guidance to understand how the rule applies to new technologies).
- Conduct internal audit dry-runs where teams simulate an audit before regulators arrive. Assign someone from your compliance or IT security team to ask tough questions and check documentation readiness.
💡Tip: Create dedicated auditor accounts in Isora so external auditors can review completed assessments, supporting documentation, and risk register entries—without full access to internal systems.
Why these extra steps matter: Here’s the thing: a risk assessment is only valuable if it inspires action. Because the real goal of a GLBA assessment isn’t just compliance—it’s about security, resilience, and proactive risk management. When consumer financial data is at stake, the cost of getting cybersecurity wrong is simply too high.
Beyond the Risk Assessment
While conducting a risk assessment against the required safeguards covers most of the mandates, there are additional steps that can enhance compliance with the GLBA Safeguards Rule and ensure a successful audit.
Manage risks in a risk register
As outlined in Step 6, compiling your findings into a risk register is an effective method to monitor gaps and coordinate remediation plans as mandated by the rule.
When using Isora, any findings that surface during your assessment can be published directly into the risk register and assigned to responsible units and people. Details like treatment, priority, impact, and liklihood can be tracked for each risk. Additionally, assigned teams can keep track of remediation plans, which serve to further illustrate your organization’s efforts towards compliance.
Make it a continuous process
The GLBA Safeguards Rule stipulates the necessity for continuous risk assessments to safeguard consumer data.
When using Isora, you can easily conduct followup SAQ risk assessments while pulling forward historical responses and evidence for continuity. Additionally, by organizing these ongoing assessments into a series, the data can be measured over time.
Demonstrating compliance to your auditor
Efficiently demonstrating compliance involves being proactive and organized. Review examination procedures from authorities like the OCC to identify potential gaps in compliance and start remediation early. Gather all necessary documentation, such as policies, risk assessments, and reports, in an accessible format for auditors.
When using Isora, auditors can be given a special role so they can access the completed assessment and results themselves.
Final Thoughts on the GLBA Safeguards Rule Risk Assessment
If it isn’t clear by now, we’ll say it one last time: a GLBA Safeguards Rule risk assessment isn’t about checking a compliance box—it’s about understanding your institution’s information security risks and doing something about them.
The truth is, these assessments often reveal more than security gaps—they show you how well (or poorly) your teams communicate, collaborate, and follow through. And if the process feels chaotic, that might be a sign your tools, workflows, or governance policies need an upgrade.
Because at the end of the day, compliance is important—but protecting the trust of your customers is everything.
Make GLBA risk assessments a more manageable, meaningful part of your security program with Isora GRC.
FAQ: GLBA Safeguards Rule Risk Assessment
GLBA Safeguards Rule risk assessments can feel overwhelming—so here are some of the most common questions we get about the process.
What are the GLBA Safeguard Rule Requirements?
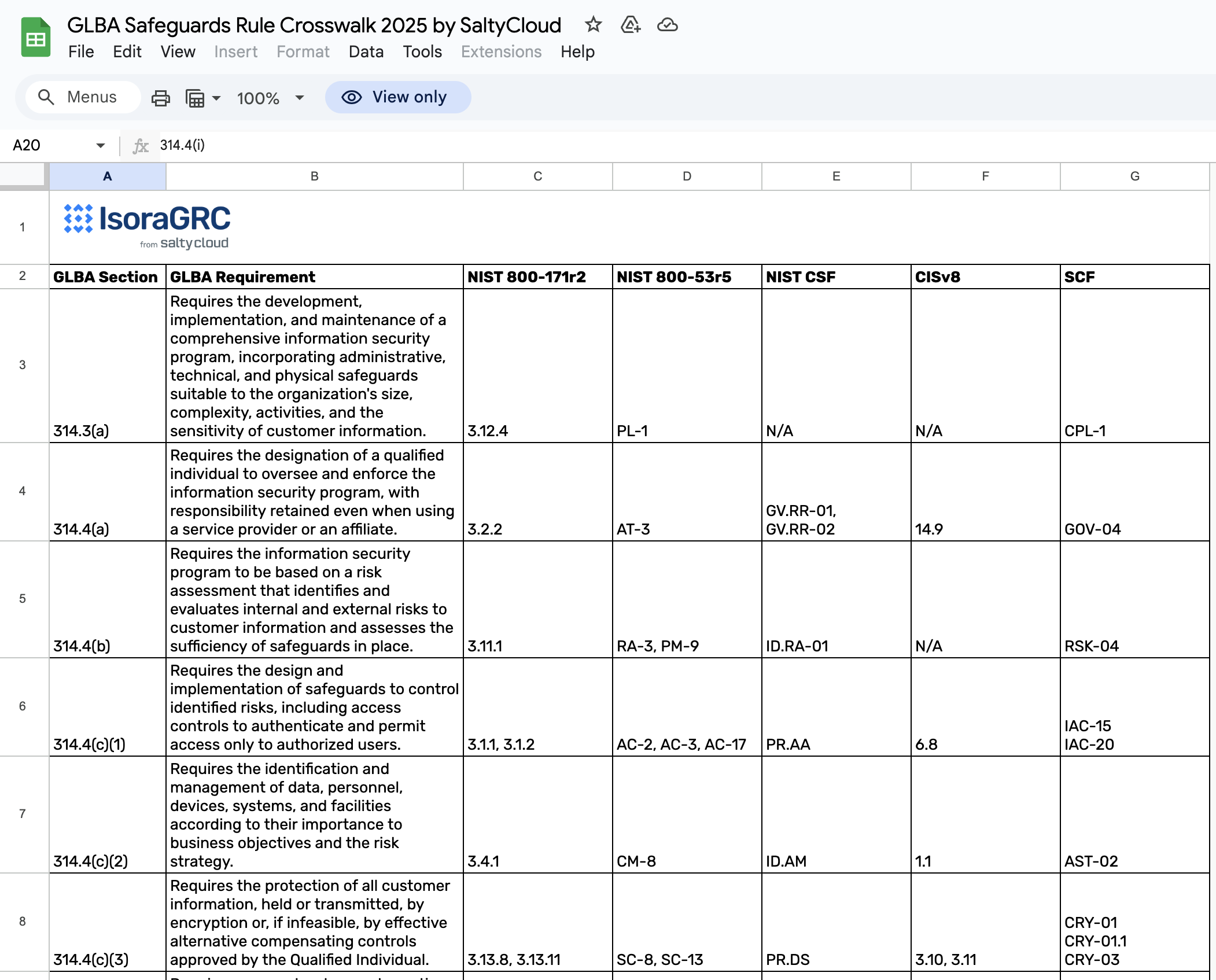
The GLBA Safeguards Rule introduces ten key elements (16 CFR 314.4) that any information security program must have for GLBA compliance.
Key elements of a GLBA-compliant information security program include:
- A Designated Qualified Individual (QI): Someone responsible for overseeing the information security program.
- Annual Risk Assessments: Periodic written risk assessments to identify, evaluate, and address security risks.
- Safeguards: Security controls to mitigate risks in key areas.
- Testing and Monitoring Capabilities: Routine tests to evaluate the effectiveness of safeguards.
- Employee Training: Security awareness training for all employees.
- Policies and Procedures: Documentation that clearly communicates these requirements.
- Vendor Management: Third-party risk management for service providers.
- Incident Response: A written incident response and recovery plan.
- Reporting: Annual written reports submitted to the governing body.
Simply meeting these requirements won’t be enough to demonstrate compliance—you’ll also need to provide the hard proof to support your claims (AKA, lots and lots of documentation).
Who must comply with the GLBA Safeguards Rule?
The GLBA Safeguards Rule applies to financial institutions of all shapes and sizes—traditional and nontraditional—that collect, process, or store consumer financial information.
Financial institutions required to comply with the GLBA Safeguards Rule include:
- Banks, credit unions, and mortgage lenders
- Insurance companies and investment firms
- Car dealerships offering financing or leasing
- Tax preparation services and accountants
- Higher education institutions handling FSA data
- Loan brokers, payday lenders, and debt collectors
- Retailers offering store credit or financing
In short, if you handle sensitive financial data, you probably need to comply.
Who enforces compliance with the GLBA Safeguards Rule?
Multiple agencies oversee GLBA compliance, depending on the institution’s size and type. Key regulators include the Federal Trade Commission (FTC), the Office of the Comptroller of the Currency (OCC), the Securities and Exchange Commission (SEC), the Commodity Futures Trading Commission (CFTC), and the U.S. Department of Education.
But these agencies don’t just audit your paperwork—they look for proof of ongoing security efforts, like regular risk assessments and remediation actions.
What happens if you don’t comply with the GLBA Safeguards Rule?
The consequences of GLBA Safeguards Rule non-compliance vary based on the severity of the oversight and the potential harm to customers. While the Safeguards Rule doesn’t list the exact fines, regulators can impose:
- Civil Penalties: Like the FTC’s multi-million-dollar fines for past violations.
- Operational Restrictions: Like suspending access to student financial aid programs.
- Reputational Damage: Because “we lost your data” doesn’t inspire trust.
The bottom line is that compliance isn’t just about following the rules to avoid penalties—it’s about protecting your customers because you care.
How often should we conduct a GLBA risk assessment?
At least once a year—but don’t stop there. You should also conduct an assessment whenever your institution…
- Implements new systems that process or store customer data.
- Adopts new technologies like cloud services or AI tools.
- Onboards new third-party vendors with access to sensitive information.
- Experiences a security incident that could impact consumer financial information.
Why is Compliance with the GLBA Safeguards Rule Important?
Compliance with the GLBA Safeguards Rule is mandatory for most financial institutions—but it’s also important for protecting customer data, preventing fines, and reducing cyber risk. Yes, GLBA non-compliance can lead to fines, legal consequences, and reputational damage. But more importantly, it can leave your customers’ data vulnerable to cyberattacks, fraud, identity theft, and more.
Why are GLBA Safeguards Rule risk assessments so challenging?
Because they involve so much more than just answering questions, the challenge isn’t just technical—it’s organizational. A successful risk assessment takes:
- Collaboration across departments, including IT, compliance, legal, and leadership.
- Detailed documentation and evidence collection for hundreds of controls.
- Regular updates and maintenance to reflect new risks or system changes.
- Ongoing education and training because people want to understand the “why” behind the “what.”
What’s the most common mistake during a risk assessment?
Skipping the follow-through. In our opinion, too many teams treat risk assessments like a one-time task when it should be a continuous process. Our recommendation? Nurture a culture of information security and build assessments into your regular operations—not just your audit calendar.
Do we need special software for a GLBA risk assessment?
Technically? No. You could use spreadsheets, emails, and shared drives. But those tools weren’t built for security teams—and you’ll likely waste weeks chasing responses, tracking evidence manually, and compiling reports from scratch.
With GLBA compliance software like Isora GRC, on the other hand, your institution can automatically distribute questionnaires and track responses, store documentation in one centralized location, generate audit-ready reports in seconds, and give teams real-time visibility into risks and remediation efforts.
Discover how Isora GRC can make GLBA risk assessments simpler, faster, and more collaborative at your organization.
This content is for informational purposes only and does not constitute legal or compliance advice. See our full disclaimer.



















 Other Relevant Content
Other Relevant Content