 Table of Contents
Table of Contents
- What is the HECVAT?
- Who Created the HECVAT?
- HECVAT Timeline
-
HECVAT Full
-
HECVAT Full: Vendor Response
- General Information
- Qualifiers
- Company Overview
- Documentation
- IT Accessibility
- Assessment of Third Parties
- Consulting
- Application/Service Security
- Authentication, Authorization, and Accounting
- Business Continuity Plan
- Change Management
- Data
- Datacenter
- Disaster Recovery Plan
- Firewalls, IDS, IPS, and Networking
- Policies, Procedures, and Processes
- Incident Handling
- Quality Assurance
- Vulnerability Scanning
- HIPAA
- PCI DSS
- HECVAT Full: Analyst Report
- HECVAT Full: Analyst Reference
- HECVAT Full: Summary Report
- HECVAT Full: Standards Crosswalk
-
HECVAT Full: Vendor Response
- HECVAT Lite
- How to Interpret HECVAT Results
- Using Isora to Simplify the HECVAT
- Recapping the HECVAT
-
HECVAT Frequently Asked Questions
- What is the HECVAT?
- What does HECVAT stand for?
- What’s the difference between the HECVAT Lite and the HECVAT Full?
- What’s the difference between SOC 2 and the HECVAT?
- Who created the HECVAT?
- Is the HECVAT mandatory for higher education institutions?
- What’s the latest version of the HECVAT?
- What if I prefer my custom HECVAT question set?

What is the HECVAT?
The Higher Education Community Vendor Assessment Toolkit (HECVAT) is a free, standardized security questionnaire for higher education institutions to annually assess third parties—like cloud service providers, on-premise vendors, and SaaS providers—for information security risks. Offering a suite of tools designed to meet different needs—including HECVAT Triage, HECVAT Lite, HECVAT Full, and HECVAT On-Premise—this resource is a great starting point for campuses looking to implement or improve security and risk assessment programs.
Colleges and universities can use HECVAT questionnaires to:
- Assess vendor services against data and security requirements for higher education
- Reduce costs without incurring more risk
- Lessen the burden on vendors
But the HECVAT is a useful tool for third parties, too. Because HECVAT assessments are free and available to everyone, vendors can conduct internal HECVAT assessments, identify areas of non-compliance, and make the necessary improvements to meet certain information security requirements—before engaging with higher education institutions.
Although this guide is intended for higher education practitioners—the IT teams, procurement officers, and compliance professionals—it can also be helpful for vendors looking to understand how higher education institutions assess third-party information security risks. No matter how you use it, this guide has everything you need to know about the HECVAT and then some.
Still wondering what the “HEC” the HECVAT is? You’ve come to the right place.
Who Created the HECVAT?
Developed by the Higher Education Information Security Council (HEISC) (now the Shared Assessments Working Group) in collaboration with EDUCAUSE, Internet2, and the Research and Education Networks Information Sharing and Analysis Center (REN-ISAC) in 2016, the HECVAT suite is regularly updated to address new and emerging risks based on community requests and feedback, with more updates expected in the future. The HECVAT 4*, for instance, launches in January 2025 and will likely include new questions for vendors about data privacy and artificial intelligence (AI), a new format, and fewer redundant or overlapping questions.
HECVAT Timeline
Here’s a timeline summarizing other important HECVAT updates:
- 2016: The Higher Education Cloud Vendor Assessment Tool is introduced as a framework for higher education institutions to evaluate the security of cloud-based products only.
- 2019: HECVAT 2 is launched, significantly changing the format from qualitative to yes/no answers with qualitative scoring. It also changed its name from “Cloud” to “Community,” added On-Premise and Triage versions, updated Full and Lite versions, and expanded the working group.
- 2020: Efforts focused on increasing adoption, improving usability, and addressing community cloud security. HECVAT also became an official EDUCAUSE HEISC community group.
- 2021: HECVAT 3 is launched with major updates, including revised questions, a stronger focus on accessibility, improved IAM content, reorganized sections, and new standards crosswalks like NIST and ISO.
- 2023: Minor updates streamlined the tool, improved documentation, and introduced mappings to Trusted CI, connecting HECVAT with frameworks for secure research.
- 2025: The anticipated HECVAT 4 (expected January 2025 launch) will introduce questions about data privacy and AI, feature a redesigned format, and reduce redundancy to simplify use.
Note: You can view all HECVAT updates using the worksheet’s Change Log tab. Or, check out our article about HECVAT updates for a comprehensive overview.
With more than 39,000 downloads in 2024 alone, the HECVAT has become a widely accepted framework for evaluating third-party information security risks. Vendors can even submit completed HECVAT assessments to the HECVAT Community Broker Index (CBI) so institutions can research and evaluate current and prospective service providers without contacting them directly.
But the HECVAT isn’t the only tool out there for assessing vendor risks in education. K-12 institutions can turn to the K-12 Community Vendor Assessment Toolkit (K-12CVAT), created by CoSN (the Consortium for School Networking). Designed specifically for primary and secondary schools, this resource is a streamlined version of the HECVAT modified to meet unique challenges in K-12 classrooms.
As educational environments grow increasingly complex, third-party risk management (TPRM) is quickly becoming non-negotiable—especially in higher ed. For many institutions, formalizing vendor risk assessment processes can feel impossible when resources are scarce, technology is outdated, and visibility is limited. Adding another layer of urgency is the sheer number of frameworks and regulations requiring third-party or service provider assessments and management today—like HIPAA, GLBA, NIST 800-53r5, NIST 800-171, PCI DSS, and Department of Education FSA-SAIG agreements, to name a few.
Yet the consequences of inaction may pose an even more significant threat—especially as fines and penalties for noncompliance grow.
Getting started now could give your organization a significant advantage over its peers as expectations around information security continue to change. For most, the first step will be comparing the HECVAT Full vs. the HECVAT Lite to determine which version best fits.
*Note: The HECVAT 4 is not yet available at the time of this article’s publication.
HECVAT Full
The HECVAT Full is the most comprehensive toolkit with 250–265 questions to help colleges and universities assess the security risks posed by third-party software and/or service providers processing large amounts of sensitive information like personally identifiable information (PII), financial records, or research data.
Unlike its condensed counterparts, the HECVAT Full is best for evaluating third-party security controls, risk postures, and defense capabilities on a more granular level. Its user-friendly format, straightforward questions, and detailed instructions make it a powerful yet simple risk assessment tool for higher education institutions and vendors alike.
The HECVAT Full worksheet is free to download as a spreadsheet and is routinely updated with new questions to reflect emerging risks. The current version, HECVAT 3.06, is organized into tabs at the top of the document, each focusing on a specific step in the vendor assessment process.
HECVAT Full: Vendor Response
The Vendor Response tab of the HECVAT Full worksheet is where software and service providers answer general and specific questions about how their company manages information security risks. Once submitted, security analysts review these answers to determine whether they comply with applicable state and federal requirements.
Questions are organized into five sections—General Information, Qualifiers, Documentation, Company Overview, and Safeguards—and grouped together by tables. Each table is structured using rows and columns and contains fillable fields where vendors can provide Yes/No answers to questions and, in some cases, additional information.
However, because some questions are nested, they can be blocked out based on a vendor’s previous answers. For the formatting logic to work, vendors must complete the first two subsections of this worksheet (General Information and Qualifiers) first.

General Information
This section captures basic yet important details like the vendor’s name, contact information, and product description.
Qualifiers
This section uses qualifying questions to help determine which additional questions are necessary and which can be nested using formatting logic for the Vendor Answer fields.
Company Overview
This section provides a snapshot of the vendor’s organizational structure, operational scope, and information security program.
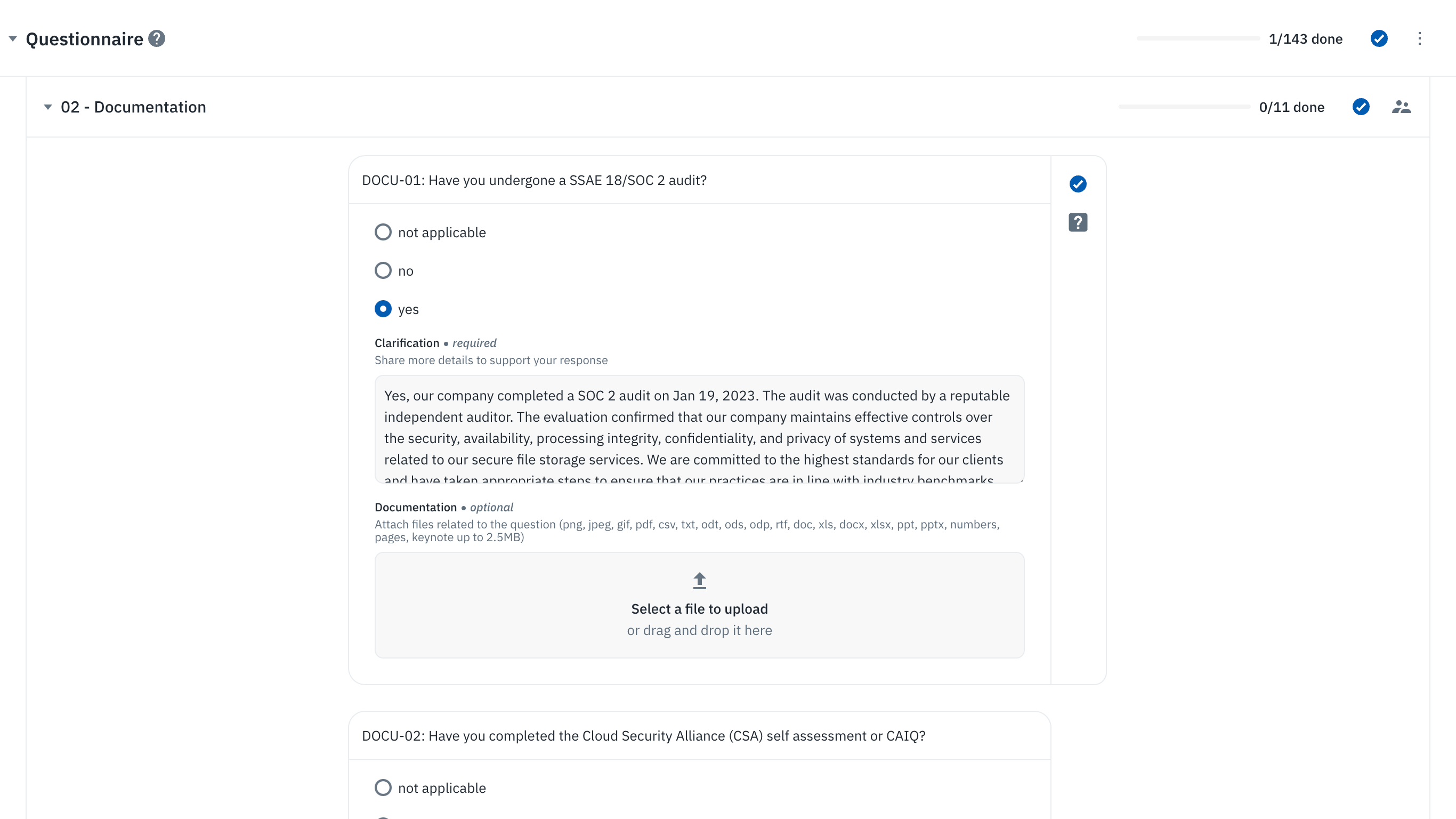
Documentation
This section contains evidence from specific reports and certifications—like SOC reports, ISO certifications, and internal risk assessments—to validate vendors’ security claims.
IT Accessibility
This section evaluates whether the vendor’s services meet IT accessibility standards by providing equitable access for all users, including those with disabilities.
Assessment of Third Parties
This section examines how the vendor manages third-party providers to ensure its subcontractors meet the same security and compliance standards.
Consulting
This section outlines the vendor’s data handling practices for consulting, advisory, and support services.
Application/Service Security
This section explores the vendor’s approach to securing applications and services, including access controls, software supply chain management, secure coding, and testing practices.
Authentication, Authorization, and Accounting
This section focuses on the vendor’s identity and access management (IAM) policies—how they control access, govern permissions, and monitor user activity to protect sensitive data.
Business Continuity Plan
This section reviews the vendor’s strategies for maintaining business operations and restoring services and data before, during, and after disruptions.
Change Management
This section looks at the vendor’s processes for implementing system updates and configuration changes—and whether they introduce risks.
Data
This section explains how the vendor handles the storage, classification, and transfer of data and whether it aligns with data protection and privacy requirements.
Datacenter
This section explores the physical security and environmental protections for the vendor’s data centers to determine whether data is stored securely.
Disaster Recovery Plan
This section reviews the vendor’s ability to recover from disasters like system outages or cyberattacks and preparedness to minimize data loss and downtime.
Firewalls, IDS, IPS, and Networking
This section covers the vendor’s network security measures—like firewalls, intrusion detection systems (IDS), and intrusion prevention systems.
Policies, Procedures, and Processes
This section documents the vendor’s security policies, risk management processes, and workflows to determine whether they’re proactive and align with industry standards.
Incident Handling
This section details the vendor’s process for identifying, responding to, and recovering from security incidents like data breaches.
Quality Assurance
This section looks at the vendor’s quality control practices and whether its products, services, and performance meet expected standards for reliability and consistency.
Vulnerability Scanning
This section investigates how the vendor identifies and addresses vulnerabilities to proactively manage and reduce risks.
HIPAA
This section covers the vendor’s compliance with the Health Insurance Portability and Accountability Act (HIPAA) and whether it handles protected health information (PHI) securely.
PCI DSS
This section determines the vendor’s compliance with the Payment Card Industry Data Security Standard (PCI DSS) and whether it processes payment data securely.
HECVAT Full: Analyst Report
The Analyst Report tab of the HECVAT Full worksheet is where security analysts assess the vendor’s qualitative responses, convert them into quantitative values, and calculate their scores. This information is often most useful during the procurement phase—before anyone signs a contract.
But higher education institutions can also use data from the Analyst Report tab at any stage of the vendor lifecycle to assess ongoing compliance with internal and external requirements. When the HECVAT 4 is published, for instance, organizations can ask vendors to update their responses and answer any new questions relating to new risks like AI and data privacy.
For additional information and guidance on interpreting questions and answers during this step, security analysts can visit the Analyst Reference tab.
HECVAT Full: Analyst Reference
The Analyst Reference tab of the HECVAT Full worksheet is where security analysts can find a detailed breakdown of each question, its purpose, and additional guidance for interpreting vendor responses. This information is particularly helpful when determining compliance states and whether to mark “Yes” or “No.” After evaluating each answer and indicating compliance, analysts can visit the Summary Report tab to determine the next steps.
Higher education institutions can also join the HECVAT Users Community Group for additional resources and to connect with peers.
HECVAT Full: Summary Report
The Summary Report tab of the HECVAT Full worksheet is where security analysts can find a high-level overview of the vendor’s assessment results and, specifically, non-compliant responses. Based on the assessment findings, institutions can follow up with the vendor for clarification or add the Summary Report output to its reporting documents and conclude the assessment.
HECVAT Full: Standards Crosswalk
The Standards Crosswalk tab of the HECVAT Full worksheet maps HEVCAT questions to compliance frameworks, including CIS Critical Security Controls v6.1, HIPAA, ISO 27002:2013, NIST CSF, NIST SP 800-171r2, NIST SP 800-53r4, PCI DSS, and Trusted CI. Higher education institutions can use this tab to evaluate how a vendor’s practices align with broader security requirements and specific industry standards.
Future versions of the HECVAT will also include updates to this tab as standards emerge and change. Importantly, HECVAT 4 will initially sunset this section until it has the resources to bring it back.
HECVAT Lite
The HECVAT Lite is a simplified version of the HECVAT Full designed for quickly assessing only the basic security practices of vendors handling low-risk data or requiring a preliminary review. This version is particularly helpful for IT teams, procurement officers, and risk managers who prioritize data protection and vendor risk management but want a less time-intensive process.
With just 62 questions, the HECVAT Lite is markedly less comprehensive than the HECVAT Full. However, it does retain enough of the core components to evaluate a vendor’s security posture effectively. Higher education institutions often use the Lite version as a first step in vendor evaluations or for vendors that don’t process sensitive information.
Like the HECVAT Full, the HECVAT Lite is free to download as a spreadsheet and is organized using tabs at the top of the document to represent each step of the assessment process. However, unlike the HECVAT Full, the Lite version does not include many sections appearing in the Full version. Although some sections are altered or missing, questions in the Lite version have been slightly reorganized to cover the gaps.
Vendors should still complete the HECVAT Lite worksheet from top to bottom to avoid errors with the formatting logic.
HECVAT Lite: Vendor Response
The Vendor Response tab in the HECVAT Lite worksheet is where vendors provide high-level details about their security frameworks. Here, the focus is on critical areas like compliance certifications, data handling practices, and security policies. Because the Lite version is significantly limited in scope compared to the Full version, it’s often easier for both vendors and institutions to complete.
General Information
This section captures the same essential details provided in the Full version: vendor name, product description, and contact information.
Company Overview
This section contains two new questions—one about HIPAA and one about PCI DSS—in addition to the five the Full version covers.
Documentation
This section also contains two new questions—one about BCPs and one about DRPs—in addition to the eleven in the Full version.
IT Accessibility
This section asks the same nine questions provided in the Full version.
Application/Service Security
This section only includes six questions compared to the Full version’s fourteen, with questions about data processing, governance, development, and security testing notably absent.
Authentication, Authorization, and Accounting
This section contains nine questions to the Full version’s nineteen for a less in-depth overview of the vendor’s IAM program.
Systems Management
This section effectively replaces the Change Management section in the Full version with just five questions about how the vendor handles activities like patch management, vulnerability scanning, and third-party security assessments.
Data
This section has seven questions, while the Full version has twenty-four, making it one of the most condensed areas of the HECVAT Lite.
Datacenter
This section contains five questions compared to the seventeen in the Full version, covering far fewer technical and operational details, specific requirements, high-level security controls, and questions about physical security.
Networking
This section—which has been renamed from Firewall, IDS, IPS, and Networking to simply Networking—asks five simple, high-level questions compared to the Full version’s eleven.
Incident Handling
This section contains one new question not asked in the Full version about whether the vendor has incident reporting processes in place.
Policies, Procedures, and Processes
This section has just three questions compared to the Full version’s sixteen for a much simpler snapshot of the vendor’s internal policies.
Third Party Assessment
This section, which occurs at the end of the Lite version and near the beginning of the Full version, asks four questions about the vendor’s third-party risk management practices, while the Full version asks five.
HECVAT Lite: Analyst Report
The Analyst Report tab in the HECVAT Lite worksheet, like the Full version, gives analysts a high-level summary of vendor responses. The instructions and order of operations are the same in both versions, with the only difference being the number of questions included in the analysis.
HECVAT Lite: Analyst Reference
The Analyst Reference tab in the HECVAT Lite worksheet, like the Full version, offers guidelines for security analysts interpreting vendor responses.
HECVAT Lite: Summary Report
The Summary Report tab in the HECVAT Lite worksheet, like the Full version, is where security analysts can find a high-level overview of the assessment’s results and areas of non-compliance. Unlike the Full version, however, the Lite version only includes six subsection scores, while the Full section provides thirteen.
HECVAT Lite: Standards Crosswalk
The Standards Crosswalk tab in the HECVAT Lite worksheet, like the Full version, maps HEVCAT questions to compliance frameworks. The only notable difference is that the Lite version uses CIS Critical Security Controls v8.1, while the Full version uses v6.1.
How to Interpret HECVAT Results
Interpreting HECVAT results isn’t for the faint of heart—it’s a complicated, tedious, somewhat subjective process. So, here’s some advice from our Andrew Scheifele, PhD, CEO & Co-Founder at SaltyCloud, CMMC Registered Practictioner, and HECVAT Review Committee Member, to help narrow your focus to the right places.
Step 1: Calculate the Overall Score
Begin with the vendor’s overall score to quickly gauge their security risk level. A high score could indicate strong compliance, but be cautious—digging deeper can help you understand whether the score aligns with your institution’s specific risk tolerance. Use this as a starting point, not the final word.
Step 2: Score by Category
Next, break down the results by individual categories, like data handling, IAM, disaster recovery, and incident response. This can help you identify which areas of the vendor’s operations are strong and which need improvement. For example, if their disaster recovery score is low, prioritize this during follow-up discussions to make sure their plans align with your institution’s needs.
Step 3: Compare with Others in the Same Vertical
Use the HECVAT’s standardized format to benchmark the vendor against others in their industry. Compare scores and responses to assess whether the vendor is keeping pace with industry standards. This can help you narrow down your choices if multiple vendors are being evaluated for the same service.
Step 4: Review High/Critical Questions with Unfavorable Responses
Pay special attention to questions flagged as high-risk or critical. These are the areas most likely to impact your institution if not addressed. For example, if a vendor struggles with data encryption standards, identify the root cause and work with them to implement the necessary safeguards before moving forward.
Step 5: Make a Mitigation Plan
For every unfavorable high or critical response, develop an actionable mitigation plan. Work with the vendor to establish safeguards, like improving access controls or scheduling regular vulnerability scans. Document these measures clearly and assign ownership for follow-up accountability.
Step 6: Document Exceptions and Follow-Up
Not every unfavorable response can be immediately resolved. For these, document exceptions in your records and decide whether to accept the associated risks. Make sure you have a clear process in place to revisit exceptions periodically to track progress.
Remember, the goal isn’t just to collect data but to harness it as a tool to improve your vendor relationships and overall security posture.
Using Isora to Simplify the HECVAT
The HECVAT is an important vendor risk assessment tool for higher education institutions—but that doesn’t make it an easy one to manage. Most of the time, that’s because organizations still gather information in spreadsheets or across different apps, which makes staying on top of all the details nearly impossible.
Simple tasks—like distributing questionnaires and collecting vendor responses—are often manual, involving time-consuming, siloed processes with communication bottlenecks. More complex tasks—like analyzing vendor responses and scoring them or engaging with vendors to address compliance gaps—can be even more challenging, especially for organizations managing vendors at scale.
Despite these hurdles, HECVAT assessments are highly recommended for higher education institutions. So why not make them simpler with Isora?
Managing HECVAT worksheets for multiple vendors is much easier with Isora GRC. Its central inventory tracks everything—from third-party vendors to IT assets, data systems, business units, and people—making it simpler to assess and follow risks.
Teams can even use Isora to distribute, collect, and analyze vendor surveys, questionnaires, and collaborative assessments all in one place. Then, they can effortlessly filter and examine findings, turn questionnaire responses into reports and scorecards, export them as PDFs and CSVs, or push them straight to the risk register for approval.
Designed to streamline GRC assessment processes for everyone—internal team members and external stakeholders alike—Isora’s people-centric platform makes it easier for organizations and their vendors to protect sensitive data with an emphasis on cross-team collaboration, data-driven risk management, and regulatory compliance.
With Isora, your organization can embrace the upcoming HECVAT 4 changes—and any added complexity—with confidence. In Isora, you can easily incorporate HECVAT 4 into vendor risk management programs, migrate vendor responses from HECVAT 3, and even quickly compare vendors so you can evaluate risks and make informed, snap decisions.
Discover how Isora can help your organization implement the security posture needed to protect everything from student records and research data to financial information and more.
Recapping the HECVAT
The HECVAT is a powerful tool—but complex for higher education institutions to evaluate and manage vendor security risks. For most organizations, navigating this resource effectively means implementing the right strategies and tools. Understanding the HECVAT’s structure and purpose—and using solutions like Isora GRC to simplify assessments—can strengthen your organization’s vendor relationships, reduce risks, and meet its security goals.
Here’s a quick recap of what we covered in our 2025 HECVAT guide:
- What the HECVAT is, how it helps with vendor risk assessment, and why it’s important for higher education institutions.
- A close examination and comparison of the HECVAT Full and Lite versions.
- How Isora GRC can help simplify HECVAT assessments at your organization.

HECVAT Frequently Asked Questions
What is the HECVAT?
The HECVAT is a standardized security questionnaire that helps higher education institutions evaluate the information security risks of third-party vendors.
What does HECVAT stand for?
HECVAT stands for Higher Education Community Vendor Assessment Toolkit.
What’s the difference between the HECVAT Lite and the HECVAT Full?
The main difference between HECVAT Lite and HECVAT Full is the level of detail: the Full version is a more comprehensive assessment of high-risk data or complex vendor relationships, while the Lite version is streamlined for vendors handling low-risk data.
What’s the difference between SOC 2 and the HECVAT?
The main difference between SOC 2 and the HECVAT is that SOC 2 is a formal audit performed by a third-party Certified Public Accountant (CPA) based on COSO principles, while the HECVAT is a vendor self-assessment questionnaire specifically designed for higher education institutions.
Who created the HECVAT?
The HECVAT was created by the Shared Assessments Working Group (formerly the HEISC Shared Assessments Working Group) in collaboration with Internet2 and REN-ISAC.
Is the HECVAT mandatory for higher education institutions?
No, the HECVAT isn’t mandatory for higher education institutions; however, it is highly recommended because it can help establish a vendor risk management program that meets the requirements for regulations like GLBA, HIPAA, CMMC, and NSPM-33. The HECVAT can also help higher ed institutions:
- Identify and mitigate vendor security risks.
- Comply with privacy laws and data protection standards.
- Build consistent, repeatable processes for evaluating third-party vendors.
What’s the latest version of the HECVAT?
The latest version of the HECVAT is HECVAT Full 3.06. EDUCAUSE announced that the HECVAT 4 will likely be released in January 2025. Once published, you can read about the latest HECVAT updates and how this version builds on previous updates.
What if I prefer my custom HECVAT question set?
While it might not check every box for your institution, a thoughtfully completed HECVAT often works better than a custom form that takes forever to get right.
This content is for informational purposes only and does not constitute legal or compliance advice. See our full disclaimer.



















 Other Relevant Content
Other Relevant Content