 Table of Contents
Table of Contents

The stakes for effective third party risk management (TPRM) have never been higher. Today, just one overlooked vendor relationship can quickly escalate into a multi-million-dollar headache (or worse, a ‘breaking news’ headline). With cyberattacks targeting third parties multiplying every year, doing more than the bare minimum is now a requirement, not an option.
No, you’re not imagining things — managing third-party risk is actually getting harder. Most of the time, that’s because most companies today have more vendors, more integrations, and more digital interdependencies than ever before. Like a bubble, unmanaged third party ecosystems stretch as they expand, becoming thin and opaque before finally bursting. Attackers that thrive on complexity already know supply chains are the weakest link — they’re just waiting for the opportune moment to strike.
The good news is you don’t have to tackle this chaos alone. Creating an effective TPRM program is much easier with a game plan. And that’s exactly what this guide offers: A clear, step-by-step roadmap filled with actionable tips, expert insights, and even a comprehensive toolkit that walks you through each step to build your own TPRM program.
Quick heads-up before we jump in: At SaltyCloud, we live and breathe third-party security risk management (TPSRM), which is why our guidance is cybersecurity-centered. But the strategies here are valuable for anyone who touches vendor relationships — IT and procurement teams, compliance managers, legal experts, operational leaders, and more. Because really, effective TPRM is about bringing the whole enterprise together to solve its most important challenges as a unified front.
Ready to untangle some third party chaos and feel confident doing it? 💪
TPRM is an acronym for third-party risk management. A TPRM program is a formalized, centralized, enterprise-wide initiative in support of the TPRM process of identifying, assessing, and remediating risks from external entities or third parties. Read our complete TPRM guide for more.
What is a Third Party Risk Management Program?
A third party risk management program is a structured, company-wide initiative designed to identify, assess, and remediate risks introduced by external entities — like suppliers, vendors, contractors, partners, and service providers. An effective TPRM program is like the ‘north star’ that guides risk management across your enterprise, uniting every touchpoint under one common goal: figuring out which third parties introduce the most risk, and reducing it before it causes measurable harm.
Ideally, successful TPRM programs will inform everything related to third party risk — the overarching guidance and principles that keep every activity aligned with the business down to the nitty-gritty instructions and workflows for every phase of the third party relationship lifecycle. For most, the best place to start will be understanding the difference between a TPRM process and a TPRM program. Gauging where your organization lands on the spectrum of TPRM maturity can help narrow focus on where there’s room to grow.
So, what’s the difference between simply having individual third party risk processes and running an actual TPRM program? Let’s find out.
TL;DR: A strong, purpose-built TPRM program isn’t just about avoiding risk. It’s about creating a strong foundation that sets your organization up for long-term success.
TPRM Program vs. TPRM Process
Contrary to popular belief, running a third party risk management process isn’t the same as having a third party risk management program. Yet, ‘TPRM processes’ and ‘TPRM programs’ often get lumped together as ‘TPRM.’ Unfortunately, this false equivalency has created a false sense of security for many. Because these terms are so often confused, some may not even realize their TPRM programs are really just a collection of disjointed processes and not a state-of-the-art program. The difference between a TPRM process and a TPRM program:
- A TPRM process: A series of ad-hoc workflows for conducting risk management activities, often completed randomly or in isolation.
- A TPRM program: An overarching, formalized initiative with well-defined governance, standardized frameworks, dedicated resources, and centralized enterprise-wide efforts.

Businesses with formal, structured TPRM programs see better outcomes — around 90% success in managing third party risks compared to the 51% using informal processes and near-zero success for those without any TPRM in place. Yet, third party security incidents still increase every year.
So, what’s the hold up? Why do so many companies today still treat third party risk management like an afterthought even though it is so obviously important?
Why Are TPRM Programs Important?
Even though third party risks aren’t exactly new, what’s different today is just how integrated, complex, and digital these relationships have become in today’s modern world. Third party relationships are a fact of life for modern businesses. Every new vendor, supplier, or software partner you engage can potentially boost innovation, improve efficiency, and introduce new opportunities. But here’s the thing: each third party relationship also comes with its own set of risks.
When your business shares sensitive information like customer records, financial data, or even internal system access, for instance, you’re trusting external entities to handle that responsibility… well, responsibly. If just one vendor experiences a cybersecurity incident or compliance slip-up, however, your organization’s data security, reputation, finances, and operations could be on the line.
Why organizations need a TPRM program today:
- More third party vendors: Globalization and digital transformation have made businesses more dependent than ever on external vendors.
- Higher stakes: Each vendor introduces potential cybersecurity, compliance, or operational risks that could directly impact your business.
- Fragmented oversight: Most businesses rely on informal, disconnected processes spread across multiple departments, creating blind spots and inefficiencies.
- Complexity at scale: As vendor ecosystems grow, manual or ad-hoc processes simply can’t keep up.
A closer look at some of these third party risk management challenges can shed light on why TPRM programs are especially important today.
Global supply chains
Companies now rely on expansive global supply chains for everything from manufacturing to digital services, expertise, and innovation. While advantageous, these third party ecosystems are incredibly complex and vulnerable to disruptions. Now, a local issue halfway around the world — like a natural disaster, sudden regulatory shift, or even geopolitical tensions — can disrupt your entire operation in ways you never saw coming.
Digital transformation
Digital transformation is also partly to blame. Today, large enterprises depend on hundreds of tools, including cloud-based software, SaaS (Software as a Service) platforms, and digital integrations. Although affordable, flexible, and easy to scale, these tools also come with a catch: Every app, platform, software program, device, and user your company uses increases its odds of cyber threats or data leaks. And, the more sensitive information your third parties can access, the greater the risk if any of it is successfully compromised.
Oversight
Most organizations today manage hundreds of third party vendors using a patchwork of spreadsheets and separate departmental processes. But when TPRM responsibilities are shared across multiple departments, there’s often no central oversight. Here, in what’s essentially the wild west of TPRM, critical third parties fly under the radar, unauthorized apps (shadow IT) abound, and teams struggle to agree on basic facts like the number of third parties they manage… Yikes. 👀
When an average of five different units share TPRM duties, this level of fragmentation can make it hard to get a complete picture. But knowing third party risk isn’t even the hardest part — it’s deciding where to focus your limited resources first. That’s precisely why a formal, dedicated TPRM program matters.
How to Simplify Third Party Risk Management
Managing third-party risks is already complex enough without the added headache of manual processes, endless spreadsheets, and scattered communication. Let’s face it — if you’re still relying on email chains, outdated docs, and that spreadsheet nobody seems to keep updated, you’re setting yourself up for stress, mistakes, and a whole lot of frustration. But here’s the good news: Simplifying your TPRM process doesn’t mean sacrificing quality. It means getting smarter about how you work. And that starts with ditching manual methods and adopting a dedicated third-party risk management solution built specifically to make your life easier.
Third Party Risk Management Software
Say goodbye to spreadsheets (seriously, good riddance 👋) and hello to Isora GRC: a centralized, user-friendly platform from SaltyCloud that automates your entire third-party risk management workflow from start to finish. Designed specifically to make vendor risk management simple yet powerful, Isora helps make sure your TPRM program scales effortlessly alongside your organization for peace of mind without extra complexity.
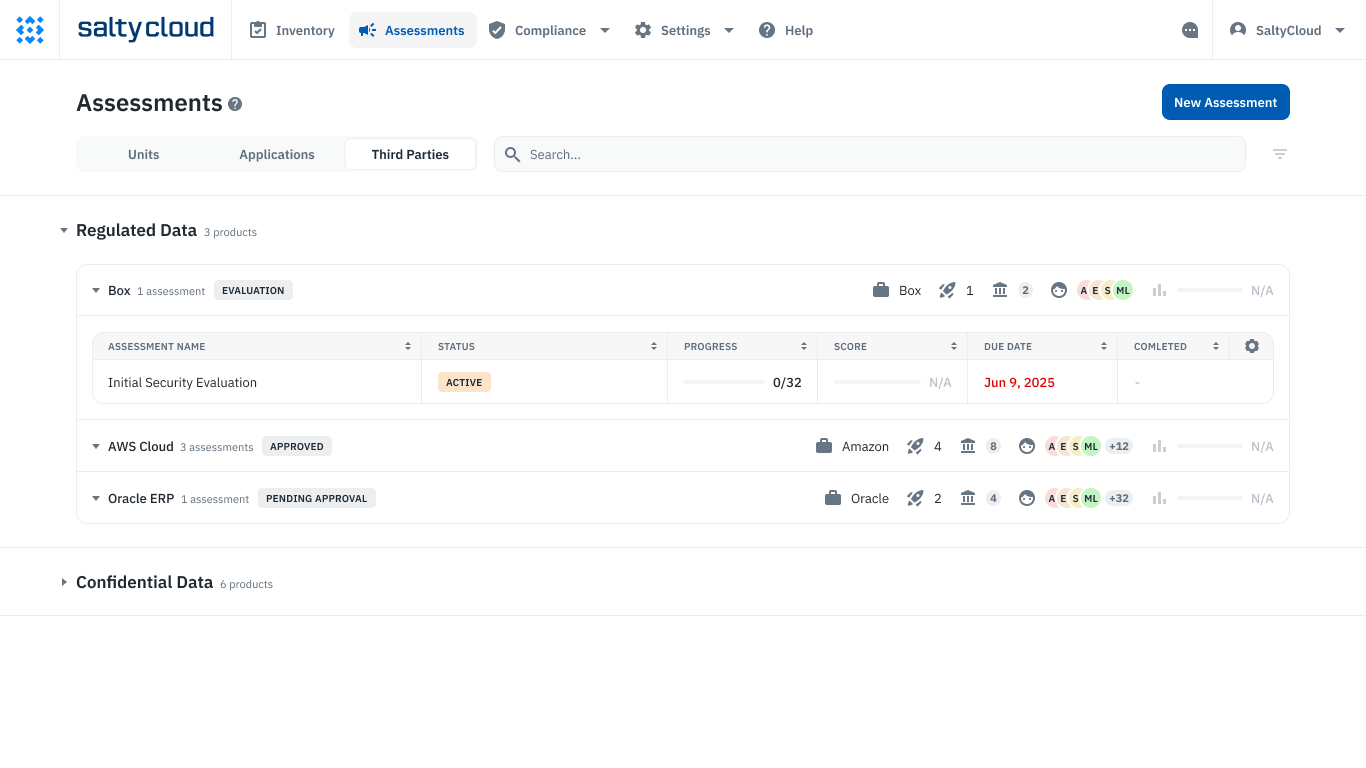
The third-party vendor assessment management dashboard on Isora GRC.
How Isora GRC helps improve TPRM:
- Automatic vendor risk assessments: Forget chasing vendors down via email. Isora GRC distributes, collects, and tracks vendor questionnaires so your team can stop pestering vendors and start actually managing risk. Vendors appreciate it too — simpler questionnaires mean quicker, more accurate responses.
- Real-time risk insights: Spreadsheets can’t tell you what changed yesterday, but Isora can. It continuously tracks your vendor ecosystem and helps your organization track risks in a central risk register — all easily accessible and at a glance.
- Centralized, searchable vendor data: No more scrambling to find last year’s assessments or worrying about missing evidence! Isora puts everything in one secure, easy-to-navigate place.
- Smarter collaboration: There’s a certain song and dance required for TPRM programs without the right tool. Internal and external teams have assessments to perform, questionnaires to fill out, evidence to upload, and approvals to confirm. Isora streamlines collaboration across internal teams and makes life easier for your third parties. Clear communication and automated reminders help everyone stay aligned, informed, and proactive.
- Reporting and scorecards: Quickly quantify and summarize vendor questionnaires and evidence so your team can make decisions faster (and more informed) than ever. Easily assess, score, and compare performances to prioritize your security compliance across the board.
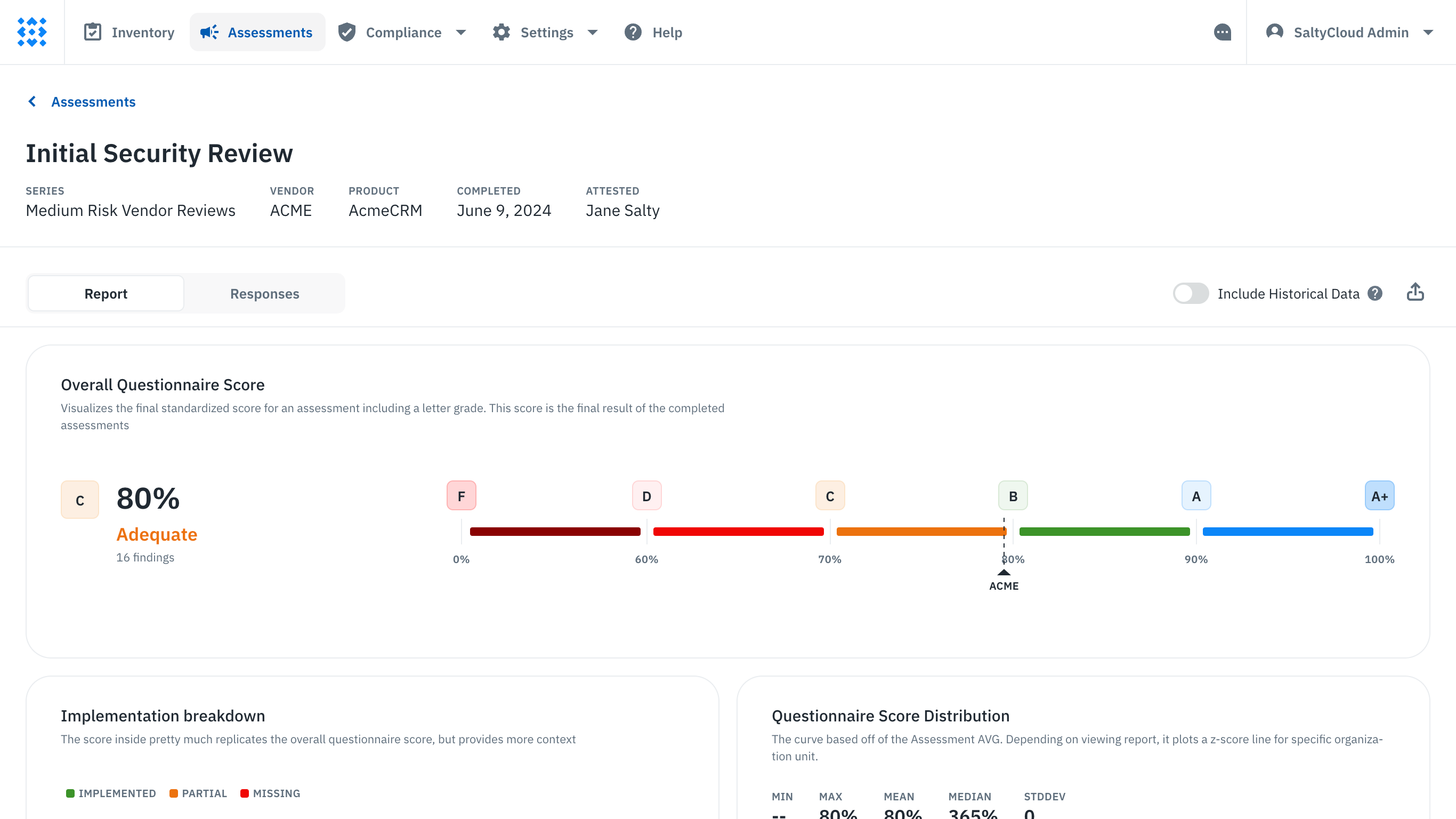
The third-party vendor scorecard report on Isora GRC.
Here’s the deal: Isora helps your team assess vendor risks with precision, track them collaboratively, and scale your third-party risk program without added complexity. Built for fast implementation and real organizational use, it works alongside your existing tools — so you can spend less time onboarding and more time reducing risk.
TPRM Program FAQs
Creating a third-party risk management (TPRM) program might feel like a big undertaking — especially as vendor networks and the threats they introduce continue to evolve. Naturally, the deeper you get into TPRM, the more questions come up. We’ve pulled together clear answers to some of the most common questions businesses ask about establishing, managing, and fine-tuning effective TPRM programs. From understanding the real costs of ineffective vendor management to securing leadership support, here’s what you need to know.
What is a third party vendor risk management program?
A third party vendor risk management program is a structured, company-wide approach to identifying, assessing, mitigating, and continuously monitoring the risks posed by external vendors and suppliers. Unlike informal processes — which might be scattered across departments or teams — a formal TPRM program provides consistent governance, standardized policies, clear roles, and dedicated tools. In practical terms, this structure helps your business keep vendor risks visible and under control across the entire lifecycle, from onboarding and ongoing assessments to eventual offboarding. By streamlining these efforts, your team can proactively reduce threats, improve vendor accountability, and consistently maintain compliance.
How often should you conduct third-party risk assessments?
Regular third-party risk assessments are essential. Typically, vendors should be assessed during initial onboarding, then reassessed annually if they’re considered lower-risk, and quarterly or semi-annually if they handle critical data, systems, or processes. But don’t limit yourself to calendar-based assessments alone — also reassess whenever a significant event occurs. Examples include vendor mergers or acquisitions, regulatory changes, major security incidents, or significant contract renewals. In short, your goal should be proactive responsiveness, not just periodic check-ins. By automating assessment scheduling and triggers within your TPRM platform, you can make sure no critical assessments slip through the cracks.
How do you evaluate the effectiveness of a TPRM program?
Evaluating your TPRM program’s effectiveness involves measuring clear, relevant metrics that align with business objectives. Consider indicators like the average time required to onboard vendors, the number of risks identified and successfully remediated, response times to security or compliance incidents, and overall internal compliance rates. Regularly comparing your results against industry benchmarks or regulatory requirements can further clarify your program’s strengths and opportunities. Ultimately, an effective TPRM program will likely demonstrate fewer high-severity incidents, quicker mitigation times when issues arise, consistently strong vendor compliance, and positive audit results.
How do you get leadership buy-in for a TPRM platform?
Securing leadership support for a TPRM platform comes down to clearly connecting your program to meaningful business outcomes. Executives are most interested in reducing financial risks, preventing costly regulatory penalties, avoiding data breaches, and protecting brand reputation. Make a compelling case by highlighting how investing in a centralized TPRM solution will
- Reduce overall organizational risk by providing proactive, real-time vendor risk intelligence.
- Avoid potential breaches or compliance issues that could lead to costly penalties or reputational damage.
- Streamline vendor onboarding and assessment processes, improving internal efficiency and reducing operational costs.
- Provide measurable, data-driven insights into vendor performance, helping the business make better-informed decisions.
Use industry examples and clear, data-backed scenarios to demonstrate tangible benefits such as cost savings, faster incident responses, and reduced compliance violations. Frame your proposal in business terms that resonate with executives — cost savings, reduced risk exposure, improved efficiency, and strengthened compliance — rather than technical details alone. A clear, practical case helps leadership quickly understand why a dedicated TPRM solution makes sense.
Dive into our research-backed resources–from product one pagers and whitepapers, to webinars and more–and unlock the transformative potential of powerfully simple GRC.
Learn More

















